Binwalk is a “firmware analysis tool designed for analyzing, reverse engineering and extracting data contained in firmware images”. This tool written in python supports Linux, and somewhat Mac OS X, can scan firmware files for files signature, and can be useful for hacking firmware files, and finding hidden information.
Let’s install binwalk first. It’s very easy in a Debian or Ubuntu machine, as you just have to download the package, and run a script for installation:
|
1 2 3 4 |
wget https://binwalk.googlecode.com/files/binwalk-1.2.2-1.tar.gz tar xzvf binwalk-1.2.2-1.tar.gz cd binwalk-1.2.2-1/src sudo ./debian_quick_install.sh |
If you have another Linux ditributions, it’s just a little more complicated. You still need to download and extract the release package as above, but you’ll have to install the following package depending on the features your need:
- Minimal installation – python 2.6 or greater, and python-magic
- To generate entropy plot graphs – python-matplotlib
- For automated extraction:
- Packages – mtd-utils zlib1g-dev liblzma-dev gzip bzip2 tar unrar arj p7zip p7zip-full openjdk-6-jdk
- Build and install firmware-mod-kit
Once, this is done, run sudo python ./setup.sh install in src directory to complete the installation.
You can also checkout the latest source code from github:
|
1 |
git clone https://github.com/devttys0/binwalk.git |
Once we’ve got binwalk installed, let’s test with the firmware for SJ1000 camera.
Just running binwalk with the firmware file as argument will scan the file for known data representations.
|
1 2 3 4 5 |
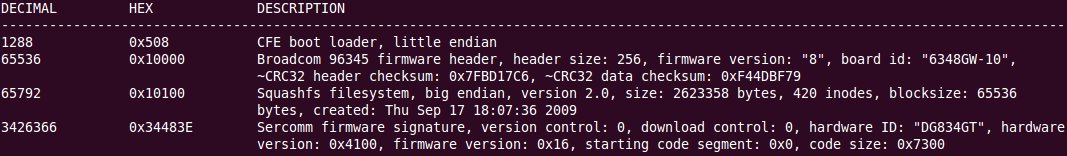
binwalk FW96650A.bin DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------------------- 2158492 0x20EF9C JPEG image data, JFIF standard 1.02 |
Right, did not find much apart from a JPEG file. I tried to extract it with binwalk -e FW96650A.bin, but it just created and empty directory (_FW96650A.bin.extracted). However, I’ve tried the scan with an Android firmware (MK908 mini PC), and the scan output is extremely verbose, it will find the Linux kernel strings, and apparently list all files. There may be options to better analyze this type of firwmare, as there are many many options, and it may take a while to be familiar with the tool.
Let’s carry on with one of the other option: ASCII string scan. In theory, the same can be achieved with strings utility, but binwalk will also provide the offset for each string in the file. In the command below, S is for string scan, and -s5 sets the minimum string size to 5 characters.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
binwalk -S -s5 FW96650A.bin DECIMAL HEX Strings ------------------------------------------------------------------------------------------------------------------- 80 0x50 NT96650 1000000020100701 192 0xC0 DRAMINFO 256 0x100 STRGINFO 116470 0x1C6F6 B0%HI 125959 0x1EC07 '^G Section-%.2ld: Range[0x%08X~0x%08X] Size=0x%08X (LOAD) 126024 0x1EC48 ^R*** StackOverflow task[%d][%s] stk start[0x%08x] size[0x%08x] 126092 0x1EC8C ^R*** Math error: type=%d name="%s" arg1=%f arg2=%f retval=%f err=%d 126164 0x1ECD4 ^R*** CPU Exception! cause=0x%08x, by [%s:0x%08x] [%c] |
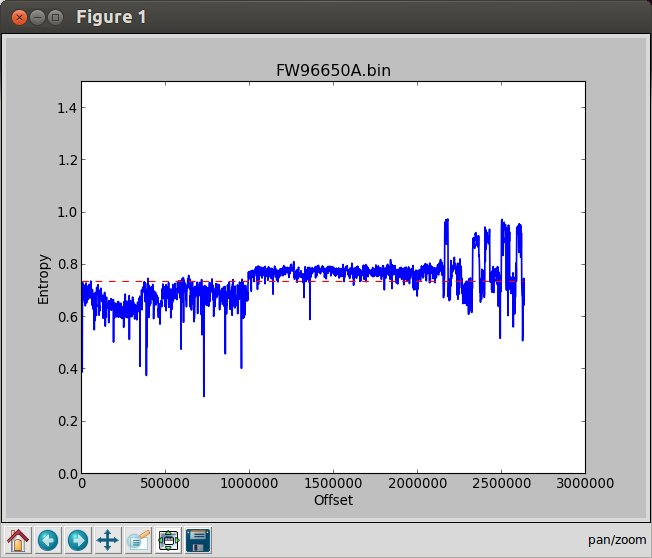
Let’s plot an entropy chart. To be honest I’m not 100% sure sure how to exploit this feature, but I understand that it will help locate where useful data may be, as well as areas filled with 0xFF or 0x00 with no useful information.
 Binwalk has lots of other features, and you can do things such as scanning a firmware image for executable opcodes, diffing multiple firmware headers, using a custom signature, and so on.
Binwalk has lots of other features, and you can do things such as scanning a firmware image for executable opcodes, diffing multiple firmware headers, using a custom signature, and so on.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress




In the same mood, you have hachoir-subfile and uwfirmforce, a quick search on my gentoo box:
* app-misc/hachoir-subfile
Available versions: ~0.5.3
Homepage: http://bitbucket.org/haypo/hachoir/wiki/hachoir-subfile http://pypi.python.org/pypi/hachoir-subfile
Description: Find subfile in any binary stream
* app-misc/uwfirmforce [1]
Available versions: 0.0.7
Homepage: http://uwfirmforce.wikidot.com
Description: uwfirmforce
Although, I usually prefer to do it manually, as the tools I’ve tried often miss the blindingly obvious stuff like gzip headers, there are a few good tools for reverse engineering.
This can be useful in the right hands –
radare – http://radare.nopcode.org/get/radare.pdf.html
arm2html – http://www.sigmaplayer.com/filebase.php?d=1&id=13&c_old=5&what=c&page=1 (assuming its still there)
file signature db – http://www.garykessler.net/library/file_sigs.html
http://www.computersolutions.cn/blog/?s=firmware has a selection of a few walkthrough’s of my detective work on various firmware.
These days, I’m concentrating more on writing my own though 😉
I am trying install Biinwalk on Portable Python 2.7 for Windows, on USB drive.
Binwalk have dependency on ssdeep-2.10, which is a binary exe (for windows).
What I dont know: where should be placed ssdeep Windows binary files, that Binwalk application can found it?