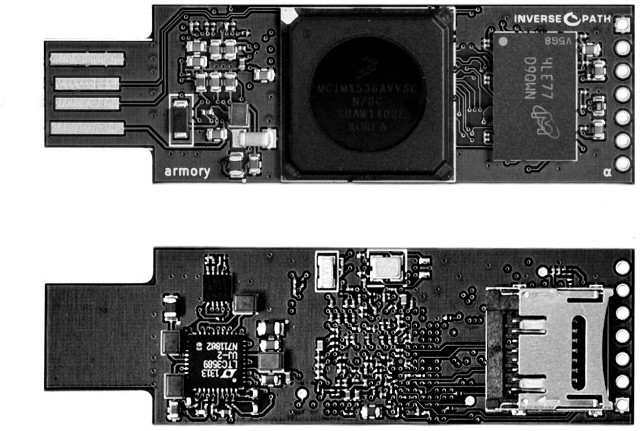
Most computers-on-a-stick come with an HDMI port, and a few USB ports, but Inverse Path’s dongle is quite different. USB Armory is a flash drive sized computer powered by Freescale i.MX53 Cortex A8 processor with only a USB port and a micro SD slot, that targets security applications such as mass storage devices with automatic encryption, virus scanning, host authentication and data self-destruct, VPN routers, electronic wallets, password managers, portable penetration testing platforms, and so on.
- SoC – Freescale i.MX53 ARM Cortex-A8 @ 800Mhz with ARM TrustZone
- System Memory – 512MB DDR3 RAM
- Storage – microSD card slot
- USB – 1x USB host port. USB device emulation: CDC Ethernet, mass storage, HID, etc.
- Expansion Header – 5-pin breakout header with GPIOs and UART
- Misc – customizable LED, including secure mode detection
- Power – 5V via USB (<500 mA power consumption)
- Dimensions – 65 x 19 x 6 mm
The board is said to run Android, Debian, Ubuntu, and FreeBSD. USB Armory is open source hardware and software, and you can already find the Kicad schematics and PCB layout files for the alpha version, distributed under a GPL v2 license, on github. Some software documentation can be found on the project’s Wiki, with firmware images coming later. Security features are achieved through ARM Trustzone which allows for secure and normal zones, and you may want to read a Trustzone on i.MX53 article on Genode OS framework project for more technical details.
USB armory is still under development, but you can register your interest on Crowdsupply where it should sell for less than 100 Euros later this year. Some more information is also available on Inverse Path’s USB Armory page.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress




Is the USB “chad” device, host, OTG, …? I don’t understand how it interacts with the OS. Device emulation? via software? How should I go about learning more about these concepts?
@Morgan Ross Egging
It’s either seen as a mass storage device (like a normal flash drive), or CDC Ethernet device (like a router), so you can run a server on that thing and access it via an IP address too. I think these are standard USB device classes.
@Morgan Ross Egging
There are USB device classes for just about everything. There is no technical reason why it couldn’t act as any kind of USB device at all, other than OTG, as it doesn’t have another power source.
@Jean-Luc Aufranc (CNXSoft)
thank you
The campaign is up on Crowdsupply -> https://www.crowdsupply.com/inverse-path/usb-armory