There’s been a lot of buzz about a root exploit in Linux 3.4 kernel for Allwinner H3/H83T SoCs found by linux-sunxi & armbian developers in the last few days. Since the kernel for H3 / H83T is stuck to 3.4, and not always updated on the vast majority of hardware platforms, it’s quite likely there are many ways to breach into such systems, and even the majority of Android devices are not secure, not only the ones powered by Allwinner. So I did not really pay attention at first, but it went viral with stories reporting a hidden backdoor, and hitting to ill-intent. But is that really the case? That’s the code from github, now removed from the master branch, but still in A83T branch.
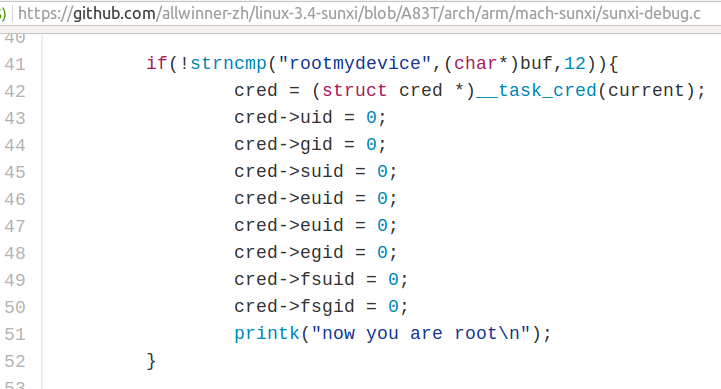 It’s now super easy to gain root access by simply running one command which works for any users:
It’s now super easy to gain root access by simply running one command which works for any users:
|
1 |
echo "rootmydevice" > /proc/sunxi_debug/sunxi_debug |
That’s obviously pretty bad, but is that a hidden backdoor? Considering Allwinner released the source code, and the kernel log would show “now you are root” each time the method would be used, that would be very stupid backdoor, and it’s not hidden since the code was there for everyone to see. A developer most probably added the code to sunxi_debug in order to ease debugging, and did not realize there was a security issue. I’ve been told the exploit only affect Allwinner H3 & A83T processors, so if you have devices with one of those, you’d better check if the exploit works, and if it does, get an updated firmware, or kernel. Using proper code review procedures, or going Linux mainline, would avoid such PR disasters. Speaking of which, Allwinner issued the following statement in response:
Allwinner Technology committed to resolving Linux Kernel software issue
Zhuhai, China – Allwinner Technology.Co.Ltd (SHE: CN:300458) is working with its device manufacturers to fix a current software issue. We are aware that code, which was supplied to device manufacturers for the purpose of developing products, should have been removed prior to shipping. We recommend that anyone who is concerned about this issue should contact the relevant device manufacturer.
In relation to the source code on Github, it is released for the open source community only and not for shipping certain devices. Since a debugging function is not needed it has subsequently been removed.
Allwinner is committed to producing quality SoCs with security a key priority. We are currently working hard to address this issue and revising our current processes so we can continue to evolve our range of SoCs in the future.
In other news, one of Pine64 managers informed me that fake/copy versions of Pine A64 development board, based Allwinner H64 SoC, had started selling on Taobao.
 It’s unclear if those are exact copies, but to be safe, you should probably avoid purchasing Pine A64 on Taobao, or Taobao forwarding services.
It’s unclear if those are exact copies, but to be safe, you should probably avoid purchasing Pine A64 on Taobao, or Taobao forwarding services.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress




something is fishy here, why one would buy the $15 advertised to be Pine64 board on taobao for $45-$75?
@Tsvetan
I don’t really understand all the number. The price seems to 299 to 499 Yuan ($45 to $76), but I can also see 59.80 to 99.80 Yuan ($9 to $15).
Agree fully with your analysis on the Allwinner issue. It is not with bad intent, but does point to a company which does not take software quality seriously. Having once spent some time on the community efforts for the A10 back in the day, I can but gloat. The way they acted back then still makes me avoid them at every turn. I like to see this issue as karma.
If the fake Pine64 on Taobao would have Micro USB replaced with a good barrel plug for DC-IN I would buy there 😉
And regarding rootmydevice let’s hope that Allwinner doesn’t move back but instead continues to release even more code (using appropriate licenses so community can do something with it). Linux-sunxi community wants to proceed with mainline kernel support for A64 and is eagerly waiting for some code only available as blob now.
@cnxsoft
“59.80 to 99.80” is advance payment, and 299-499 is total payment. I am a chinese in Hangzhou.
@tkaiser
maybe you know, they (pine64) sell usb cable on their shop, is it good for powering the board?
@cortex-a72
At least it’s rated 20 AWG (less resistance) but with Micro USB for DC-IN a few more problems are associated (like encouraging users to choose the wrong PSU). Pine64 forums are flooded with boot problems and this list here is not even complete: http://forum.pine64.org/showthread.php?tid=514
@tkaiser
and my own little recent anecdotes about micro USB ports:
1. My first attempt at booting MiQI board, failed until I got the right micro USB cable and power supply combination
2. Wio Link (ESP8266 board) refused to boot when connected to my USB hub, but that was fixed when I changed that to the same micro USB cable and power supply as used on MiQi.
This would never have happened if commit history would have been pushed along with the changes. A 3k pull request that merger only has a single comment to work with isn’t enough to go by. It might have been fine a decade ago when static analysis tools were so bad and rare that every working merge requests have gone through very thorough reviews… But nowadays huge amounts of C code can be committed without a second glance and reading through it is often too time consuming to ever get done.
@RK
Never say never. Security issues are getting discovered on a regular basis even in the mainline kernel and other respectable open source projects. But yes, it is always possible to do a better job by adhering to good practices and allocating more time/resources.
@tkaiser
thank you.
(I also am happy when a board has dedicated power jack, and a normal PSU in the kit.)
Debating whether this was was malicious or not misses the entire point. There is _NO_ reason/excuse for any developer to ever put something like this into kernel source much less push it into a distribution. “But they may have needed to debug something.” If that’s the case, they would have had root access to the box. The only reason to put something like this in is to get access to a box you don’t have privileges on.
Little update how SBC vendors affected by this exploit did react in the meantime (Armbian team opened Github issues where possible 16 days ago). The only ones rolling out new OS images besides Armbian are SinoVoip (they also provide a way to update the kernel for BPi M2+/M3 images but that’s so complicated/weird that most probably no one of their users is able to follow the instructions).
Some vendors reacted and deactivated the exploit code in their Github repos without providing any fixes to their users, two still ignore the whole issue (LinkSprite and Xunlong) but no one thought about informing users and providing a quick workaround until a real fix has been rolled out like setting in a start script something like this:
chmod 000 /proc/sunxi_debug/sunxi_debug
But to be honest. At least the few Orange Pi OS images I tried out so far before we started to support H3 in Armbian were so horrible regarding security that it really doesn’t matter that much whether fix/workaround is applied or not (only Armbian/OpenELEC upgraded sun8i BSP kernel to 3.4.112, all the others still remain at 3.4.39 for no other reason than laziness, all OS images except of one I tried out before allow sudo without authentication, none of them regenerates SSH host keys so man-in-the-middle attacks are possible and so on. Of course most of the aforementioned applies to SinoVoip’s OS images for BPi M3 too)