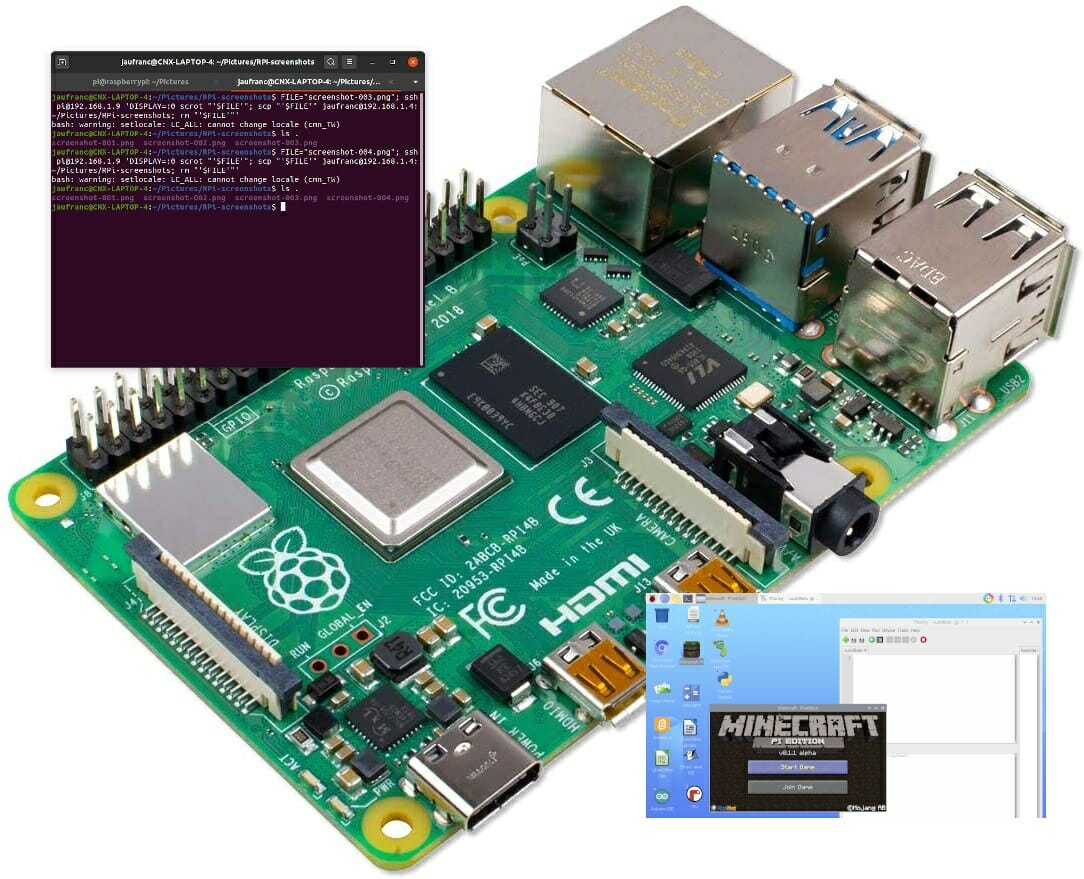
I recently reviewed a Raspberry Pi 4 laptop with a custom interface that made it impractical to take screenshots directly on the device. So instead I had to take screenshots remotely over SSH. It’s quite easy to do. Most of the steps can be reproduced in other Linux systems, and are not specific to Raspberry Pi. Enable SSH in Raspberry Pi First, enable SSH either with sudo raspi-config in a terminal window and selecting 5. Interface Options, then P2 SSH… If for some reason, you don’t have access to the terminal, take out the MicroSD card from the Raspberry Pi board, and from a computer create a new empty file named “ssh” in the boot partition. Now provided you have the username and password for your board, you can connect to SSH with the IP address from a terminal:
|
1 |
ssh <username>@<ip_address> |
or a program like Putty. Taking a screenshot remotely You’re […]