In the first article, I checked out the hardware of the Chatreey AM08 Pro mini PC powered by an AMD Ryzen 9 7940HS CPU and tested it with Windows 11 Pro in the second part of the review. Now it’s time for the third part where I’ll test Ubuntu 22.04.03 Desktop OS and ESXi 7.0 update 3C hypervisor on the AM8 Pro mini PC. The installation process was simple enough and both WiFi and Ethernet were detected correctly. Contents Ubuntu 22.04 System information with AM08 Pro Performance of AM08 Pro 7940HS sbc-bench.sh Geekbench iozone3 FIO Network performance (2.5GbE and WiFi 6) of AM08 Pro 7940HS 2.5 GbE WiFi 6E Stress test and CPU temperature of AM08 Pro 7940HS Power consumption of AM08 Pro 7940HS Jellyfin on Ubuntu 22.04.03 (server) ESXi 7.0 Installation The stability Conclusion 1. Ubuntu 22.04 1.1. Ubuntu System information with AM08 Pro The system information in Ubuntu […]
How to use a monitor and USB mouse/keyboard in Promox VE on an Intel Alder Lake-N mini PC
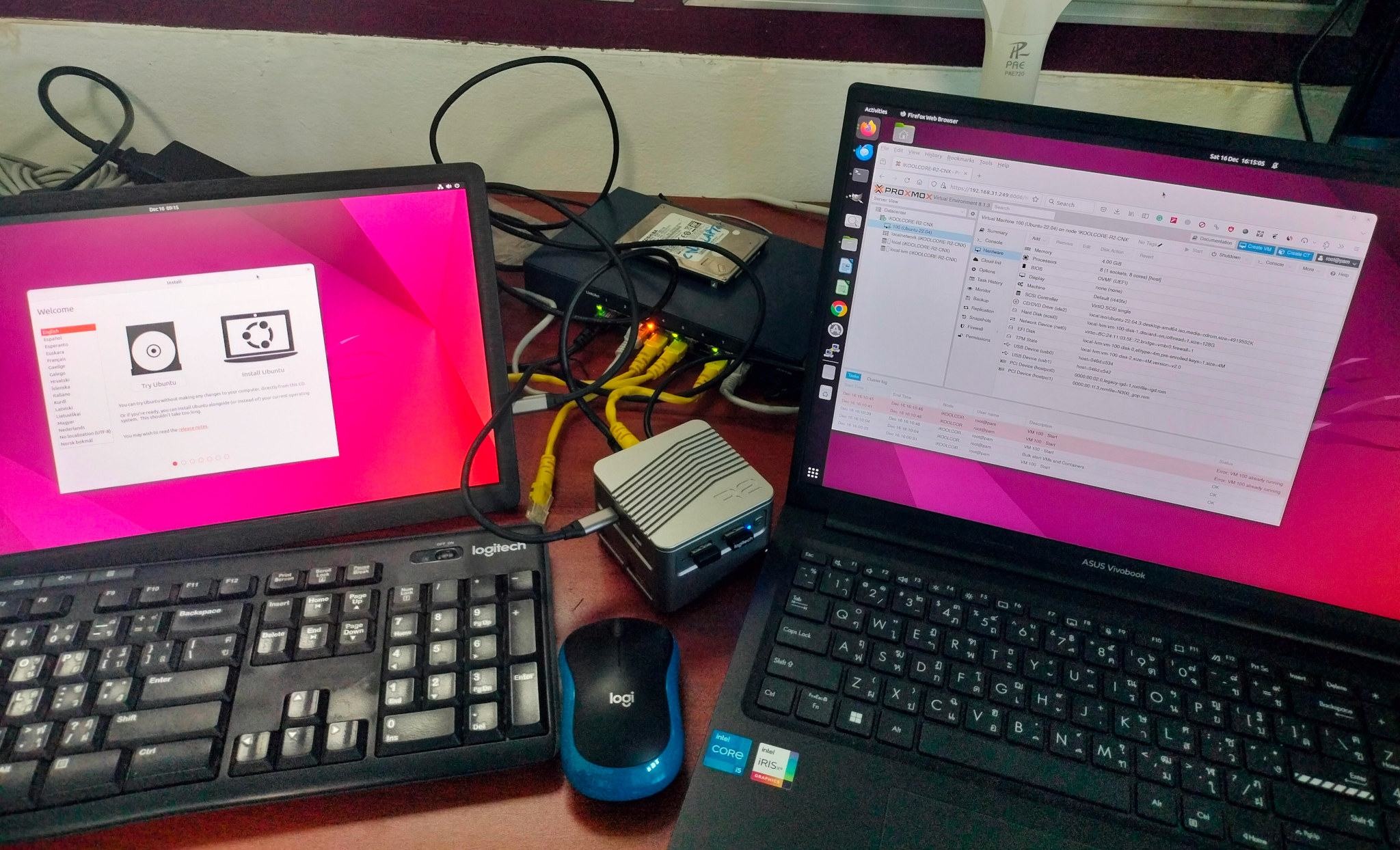
We’ve started to see several Alder Lake-N platforms acting both as a mini PC and a router or network appliance with products such as iKOOLCORE R2 or CWWK x86-P5 which features not only the usual HDMI, USB, and single Ethernet port, but come with multiple Ethernet ports making them ideal to run Proxmox VE to simultaneous run a desktop OS such as Ubuntu 22.04 or Windows 11 and a headless network OS such as pfSense or OpenWrt. I’m currently reviewing iKOOLCORE R2 mini PC that comes with four 2.5GbE ports and I could install Ubuntu 22.04 Desktop, pfSense 2.7.1, and OpenWrt 23.05 relatively easily, but the Ubuntu desktop is only visible in the Proxmox VE dashboard and the HDMI display physically connected to the mini PC only shows Proxmox VE login prompt. So at this point, I learned that I had to enable PCIe passthrough for the GPU in Proxmox […]
Beelink EQ12 Review – An Intel Processor N100 mini PC tested with Windows 11, TrueNAS, pfSense, Ubuntu, and more
Beelink’s new EQ series of mini PCs form their base product range and feature low-powered Jasper Lake and Alder Lake-N processors with relatively basic port and memory/storage configurations. Perhaps more importantly, they are also the cheapest mini PCs they offer. Having recently announced the EQ12 mini PC featuring an Intel Processor N100 ‘Alder Lake-N’ CPU with up to 16GB RAM, Beelink have now sent one for review. Whilst I’ll cover the basic Windows operation and performance, I’ll also explore how this new mini PC performs when used as an integrated router and NAS. Beelink EQ12 specifications Beelink list the EQ12 specifications as: It is worth noting that the Processor N100 processor only supports a single memory channel and that according to Intel’s specification for the processor, the maximum memory supported is only 16 GB. Intel’s specification for the number of graphical execution units (EUs) also states 24 however software such […]
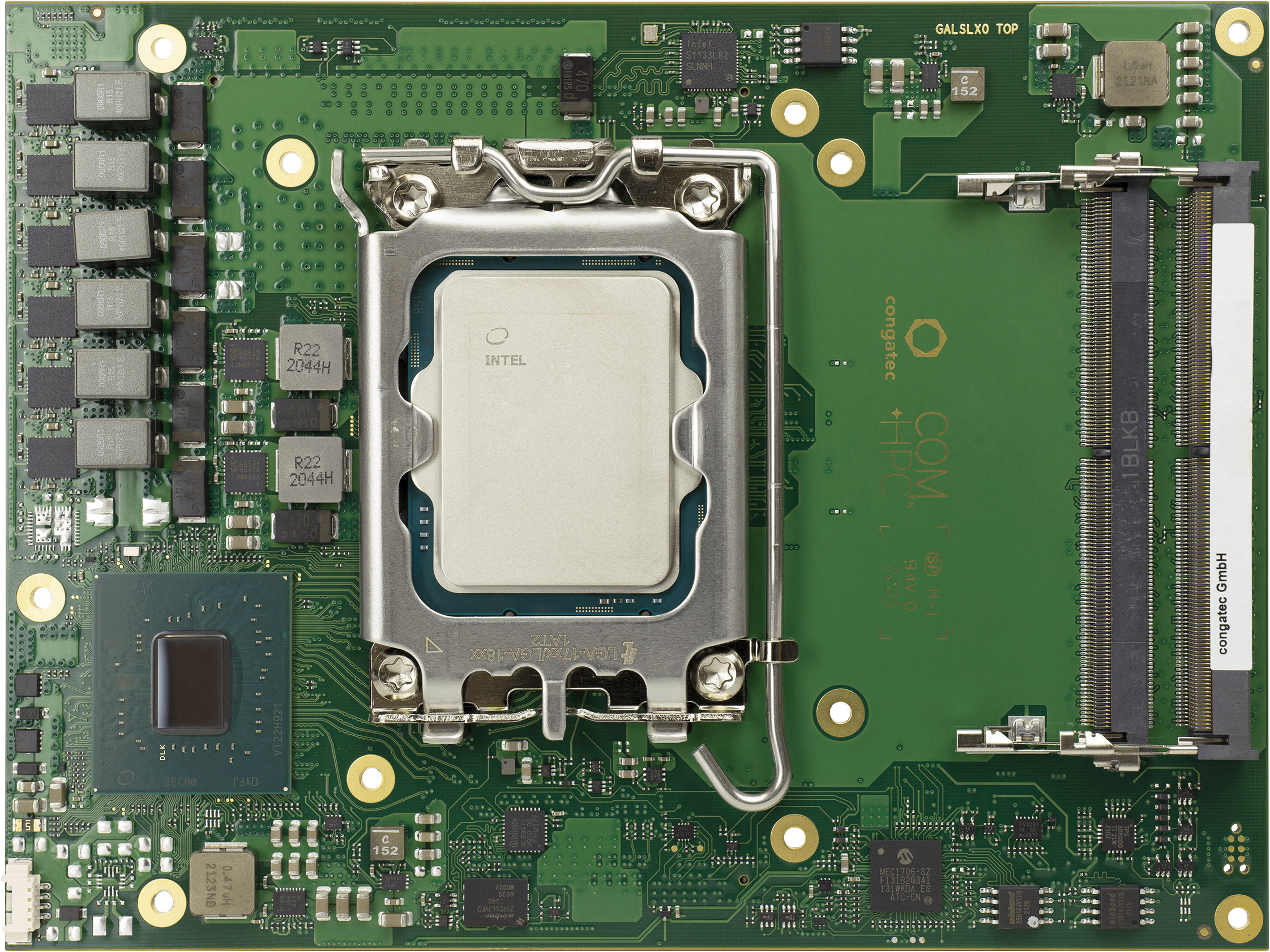
conga-HPC/cRLS Raptor Lake COM-HPC Client module supports up to 128GB DDR5 RAM
Congatec conga-HPC/cRLS is a COM-HPC Client Size C computer-on-module based on a 13th gen Intel Raptor Lake processor with support for up to 128GB DDR5 memory through four SO-DIMM sockets. The COM-HPC module also provides up to three DDI display interfaces, two 2.5GbE networking interfaces with TSN support, two SATA storage interfaces, and a range of PCIe Gen 3, 4, and 5 interfaces through the two 400-pin connectors defined in the COM-HPC standard. conga-HPC/cRLS specifications: Raptor Lake-S SoC (one or the other) Intel Core i3-13100E with 4x P-cores @ 3.3GHz / 4.4GHz, 12 MB cache, Intel UHD Graphics 730; PBP: 65W Intel Core i5-13400E with 6x P-cores @ 2.4GHz / 4.6GHz, 4x E-cores @ 1.5GHz / 3.3GHz, 20MB cache, Intel UHD Graphics 730; PBP: 65W Intel Core i7-13700E with 8x P-cores @ 1.9GHz / 5.1GHz, 8x E-cores @ 1.3GHz / 3.9GHz, 30MB cache, Intel UHD Graphics 770; PBP: 65W Intel […]
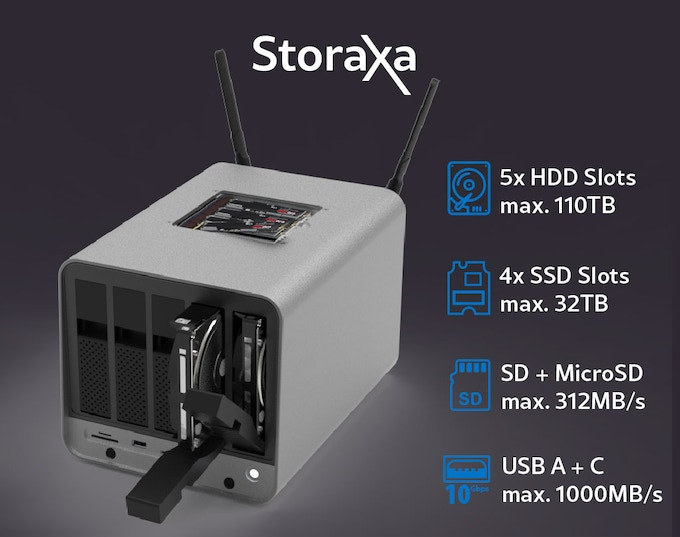
Storaxa is a 3-in-1 5-bay NAS, WiFi 6 router, and 4K media center (Crowdfunding)
The Storaxa is a multi-purpose device powered by an Intel Celeron N6005 Jasper Lake processor which works as a 5-bay SATA NAS, which also happens to take up to four NVMe SSDs, a 4K media center with HDMI and DisplayPort interfaces, and a WiFi 6 router equipped with four 2.5GbE ports. The solution is fitted with 16GB RAM, comes with four 10 Gbps USB 3.2 ports and two USB 2.0 ports, and runs Proxmox VE to handle both TrueNAS SCALE and OpenWrt for the NAS and router functions respectively. Storaxa specifications: SoC – Intel Celeron N6005 quad-core Jasper Lake processor @ 2.0GHz / 3.3GHz (Turbo) with 32EU Intel UHD graphics @ 450 / 900 MHz (Turbo); 10W TDP System Memory – 16GB (2x 8GB) DDR4-3200 SO-DIMM memory Storage 128 GB SATA SSD for OS 5x 3.5-inch SATA bays 4x M.2 2280 sockets for NVMe SSDs (connected via ASMedia ASM2812X PCIe […]
Linux 5.19 Release – Main changes, Arm, RISC-V and MIPS architectures
Linus Torvalds has just announced the release of Linux 5.19. It should be the last 5.xx version, with Linux 6.0 coming for the next cycle: So here we are, one week late, and 5.19 is tagged and pushed out. The full shortlog (just from rc8, obviously not all of 5.19) is below, but I can happily report that there is nothing really interesting in there. A lot of random small stuff. In the diffstat, the loongarch updates stand out, as does another batch of the networking sysctl READ_ONCE() annotations to make some of the data race checker code happy. Other than that it’s really just a mixed bag of various odds and ends. On a personal note, the most interesting part here is that I did the release (and am writing this) on an arm64 laptop. It’s something I’ve been waiting for for a _loong_ time, and it’s finally reality, […]
Embedded World 2022 – June 21-23 – Virtual Schedule
Embedded World 2020 was a lonely affair with many companies canceling attendance due to COVID-19, and Embedded World 2021 took place online only. But Embedded World is back to Nuremberg, Germany in 2022 albeit with the event moved from the traditional month of February to June 21-23. Embedded systems companies and those that service them will showcase their latest solution at their respective booths, and there will be a conference with talks and classes during the three-day event. The programme is up, so I made my own little Embedded World 2022 virtual schedule as there may be a few things to learn, even though I won’t be attending. Tuesday, June 21, 2022 10:00 – 13:00 – Rust, a Safe Language for Low-level Programming Rust is a relatively new language in the area of systems and low-level programming. Its main goals are performance, correctness, safety, and productivity. While still ~70% of […]
Arm SystemReady SR-certified Ampere Altra Developer Platform launched for $3,999
ADLINK has just announced the availability of the Arm SystemReady SR-certified Ampere Altra Developer Platform equipped with the company’s COM-HPC Ampere Altra module with 32 to 80 64-bit Arm Neoverse N1 cores, 32GB to 128GB RAM. An adaptation to the earlier AVA Developer Platform expected to sell for $5,450, the Ampere Altra Developer Platform got a price cut to $3,999 at launch for a system with a 32-core processor, and 32GB DDR4. The system targets software developers wanting to build cloud-to-edge applications using standardized Arm hardware. Ampere Altra Developer Platform specifications: SoM – COM-HPC Ampere Altra module with Ampere Altra 32 to 80-core 64-bit Arm Neoverse N1 processor up to 1.7/2.2/2.6 GHz (32/64/80 cores, TPD: 60W to 175W), 32 GB to 128GB DDR4 ECC memory Storage – 128 GB NVMe M.2 SSD Mainboard – COM-HPC Server Base carrier board Video – VGA port Audio – 3.5mm audio jack Networking 1x […]