Qingping CGDK2 and Xiaomi LYWSD03MMC Bluetooth LE (BLE) temperature and humidity monitors based on Telink TLSR8258 can be switched to Zigbee thanks to a custom firmware flashed over-the-air. Telink TLS8258 is a multi-protocol wireless microcontroller supporting Bluetooth LE 5, Bluetooth Mesh, Zigbee, RF4CE, Thread, 6LoWPAN, HomeKit, ANT, and 2.4GHz proprietary and found in boards such as the LILYGO T-Zigbee and various products. Some products only enable one wireless protocol, for example, Bluetooth LE as in the just-mentioned Qingping and Xiaomi monitors, but “SmartHomeScene” has found out that it was possible to switch from BLE to Zigbee on those by simply updating the firmware. The Telink TLS8258 devices mentioned above will publish data over BLE every 10 minutes (unless humidity or temperature changes, in which case data is transmitted immediately) with the default firmware, but Zigbee can be enabled by using the pvvx custom firmware for the following models: Xiaomi LYWSD03MMC […]
LoLRa project – Transmitting LoRa packets without radio using CH32V003, ESP8266, or ESP32-S2 MCU
The LoLRa project is a firmware-only LoRa transmission open-source project that works without a Semtech radio and instead relies on an I2S or SPI interface (so not exactly bit-banging) to transmit data with microcontrollers such as WCH CH32V003, or Espressif Systems ESP8266 and ESP32-S2 microcontrollers. LoRa is a proprietary protocol by Semtech, but people have been trying to reverse-engineer the LoRa PHY for years, and this culminated with a LoRa GNU Radio SDR implementation last year. But CNLohr found out you don’t even need a radio to send LoRa packets and you can instead use SPI or I2S interfaces from general-purpose microcontrollers to send packets that can be decoded by commercial off-the-shelf LoRa gateways and other chips. The current implementation is designed for the ITU Region 2 (aka The Americas) targeting the 902-928MHz frequency band, but the code could be changed for Region 1 (EU, Russia, Africa) to target 863-870MHz […]
Some Raspberry Pi 5 boards can be overclocked up to 3.14 GHz (and run just fine)
The Raspberry Pi 5 is advertised as a single board computer with a CPU clocked up to 2.4 GHz, but some of the boards can run stably at a higher frequency, and Jeff Geerling found out one of his boards could be overclocked up to 3.14 GHz with no issues when running a stress test. The Raspberry Pi 5 already delivers a two to three-times jump in performance against the previous generation Raspberry Pi 4 SBC when clocked at 2.4 GHz, but some already overclocked their up to 3.0 GHz, and many thought it was the maximum limit. But a recent firmware release proved them wrong, as it turns out some Raspberry Pi 5 boards can boot at 3.2 GHz and run stably at 3.14 GHz with an adequate cooling solution. The voltage was also adjusted in the config.txt to more or less safe settings. Contrary to the photo above, […]
Flipper Zero gets a Raspberry Pi RP2040-powered video game module
Flipper Zero hardware & wireless hacking tool can now be used as a proper game console thanks to a Raspberry Pi RP2040-powered video game module that mirrors the display of the device on a larger monitor or TV via DVI/HDMI video output, and also adds a 6-axis motion tracking sensor. The Flipper Zero has been in the news in recent days, notably with Canada’s government banning the device due to car theft (although it only seems feasible on older cars), and today the company has announced the launch of a video game module developed in collaboration with Raspberry Pi Ltd. Video game module specifications: MCU – Raspberry Pi RP2040 dual-core Arm Cortex-M0+ microcontroller clocked up to 133 MHz with 264 kB SRAM Video Output – DVI-D at 640х480 with 60 Hz refresh rate. It also supports HDMI. USB – USB Type-C port connected to the microcontroller. Acts as a USB device […]
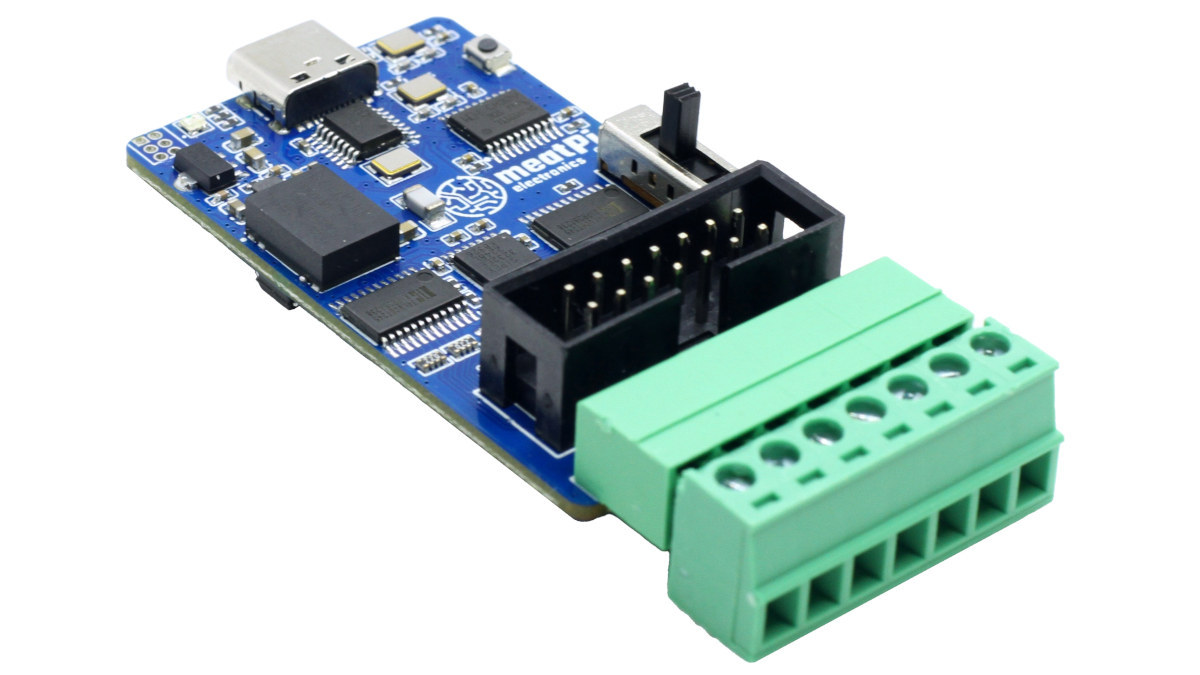
Ollie v2 USB to UART/CAN/RS485/RS232 converter gets USB-C port, plastic enclosure, and more (Crowdfunding)
Ollie v2 is an improved version of the Ollie USB to isolated UART, CAN Bus, RS232, and RS485 converter that gains a USB-C port, a plastic case, the ability to set the voltage from the target board, and various other minor improvements. Like the first version, the Ollie v2 is a portable tool designed for hackers and field engineers that allows them to work with a single device instead of a bunch of USB converters, each handling a single protocol, and isolation makes sure the host, such as a laptop, is protected from high voltages. Ollie V2 specifications: Serial chip – WCH CH344 quad-serial port chip (instead of XR21V1414 in the first design) Host interface – USB Type-C port Isolated interfaces (all with ESD protection) 2x UART ports up to 6 Mbps with 1.8/3.3/5 V or target voltage levels (set by slide switch) CAN 2.0A/B up to 1 Mbps bus […]
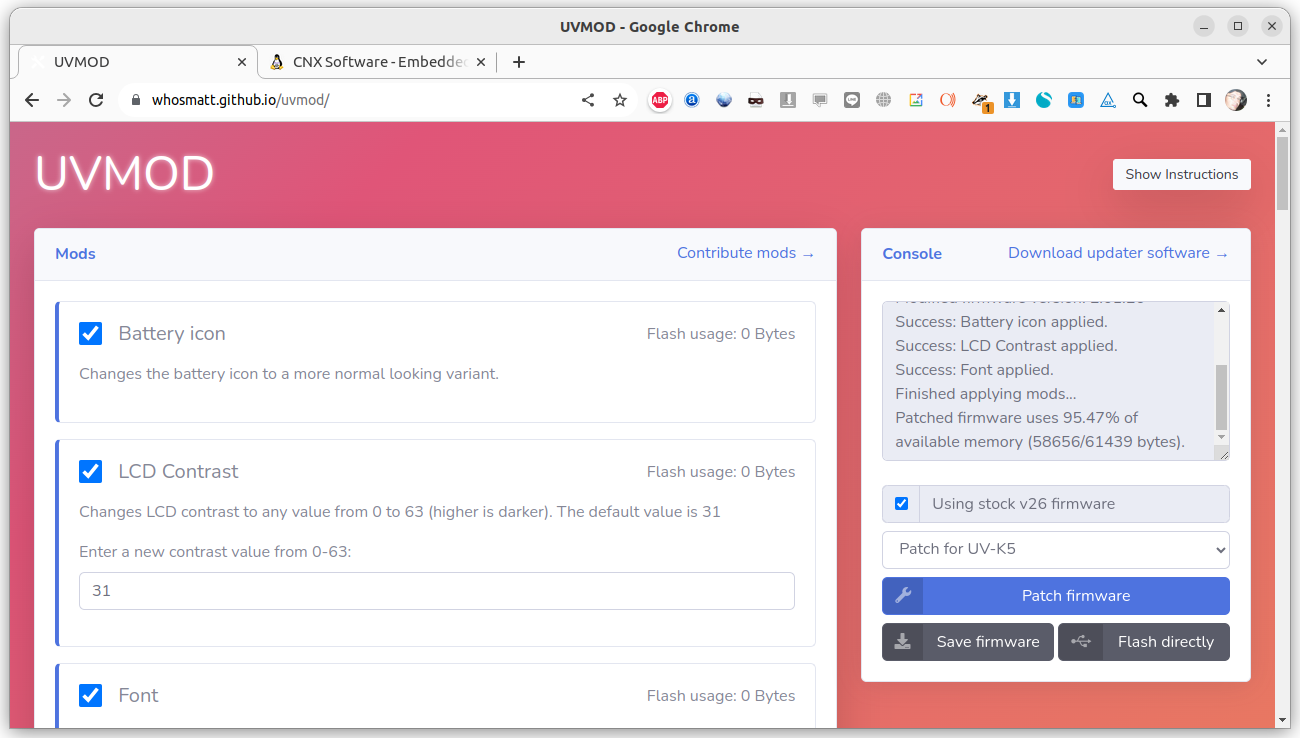
Quansheng multiband radios’ firmware can be flashed and customized from a web browser
We’ve recently written about the Quansheng UV-K5 multiband radio which supports experimental firmware to work in a wider 18 MHz – 1300 MHz frequency range than with the stock firmware so it can be used for amateur radio, air traffic control, Citizens Band (CB) radio, and other fun stuff. But flashing the firmware requires downloading the manufacturer’s Windows-only programming software and customizations are provided through multiple firmware files. But it has now become much easier to flash the firmware for Quansheng devices thanks to the work of whosmatt who developed the UVMOD web interface using WebSerial to flash the firmware and even customize it from Windows or Linux. The interface supports Quansheng UV-K5, UV-K6, UV-K5(8), and UV-5R Plus handheld radios, and you’ll need a web browser that supports the WebSerial API to flash the firmware directly from the web browser directly, which means only the desktop versions of Chrome, Edge, […]
Flipper Zero hardware & wireless hacking tool gets an app “store” with open-source app
Flipper Zero portable multi-tool for pentesters and hardware hackers has now gotten an app “store” with currently around 100 free and open-source apps available through the device’s Android or iOS app. I missed it at the time, but the Flipper Zero launched on Kickstarter in July 2020 and was massively popular with close to 5 million dollars raised from almost 38,000 backers. The tool looks like a toy but it allows hacking with GPIOs and short-range wireless protocols such as Bluetooth, RFID, NFC, and infrared. Flipper Zero specifications: Wireless MCU – STMicro STM32WB55RG with Arm Cortex-M4 application core @ 64 MHz, Arm Cortex-M0+ network core @ 32 MHz, 1024 KB flash, 256KB SRAM Storage – MicroSD card slot up to 64GB Display – 1.4-inch monochrome LCD (black on orange background) with 128×64 resolution via ST7565R SPI display controller Connectivity Bluetooth 5 LE & 802.15.4 via STM32WB55 microcontroller Bluetooth LE – […]
Quansheng UV-K5 multiband radio gets experimental firmware to work in the 18 MHz – 1300 MHz bands
Quansheng UV-K5, an inexpensive walkie-talkie/multiband radio that works in the 50 MHz to 600 MHz bands, has gotten an experimental firmware from the community that expands the range to 18 MHz to 1300 MHz, the maximum limits of the Beken BK4819 chip it is based on. The device is popular enough in the ham radio community that an unofficial blog has been created for it. The author explains that UV-K5 is better than other typical Chinese radios with “intuitive controls although the naming is a bit cryptic, and a nice crisp display”. He goes on to explain how to flash the firmware and reminds users they do this at their own risk in case they brick the device or break any regulations. The Quansheng UV-K5 supports the following bands with the stock firmware: F1: 50.0000-76.0000MHz (RX only) F2: 108-.0000-135.9750MHz (RX only) F3: 136.0000-173.9750MHz (TX and RX both) F4: 174.0000-349.9750MHz (RX […]