I have reviewed two Reolink WiFi IP cameras in recent years: Reolink Argus Eco and Reolink Argus PT. Both are powered by solar panels, and they’ve been running at home for many months, but there are many false positives, or on the contrary, sometimes the PIR sensor fails to detect people. What would solve this is built-in AI into those surveillance cameras. The good news is that Reolink RLC-810A does just that with the ability to detect persons and/or vehicles, so you would not receive a notification because some bird or insect flew in front of the camera. I’ve just received a review sample, so I’ll part by listing the specs and features, and unboxing the package to see what the camera looks like, and check out included accessories. Reolink RLC-810A specifications Video & Audio Image Sensor – 1/2.49″ CMOS Sensor Video Resolution – 3840×2160 (8.0 Megapixels) at 25 frames/sec […]
OPTIGA Trust-M evaluation kit for Raspberry Pi targets Connected Home over IP standard
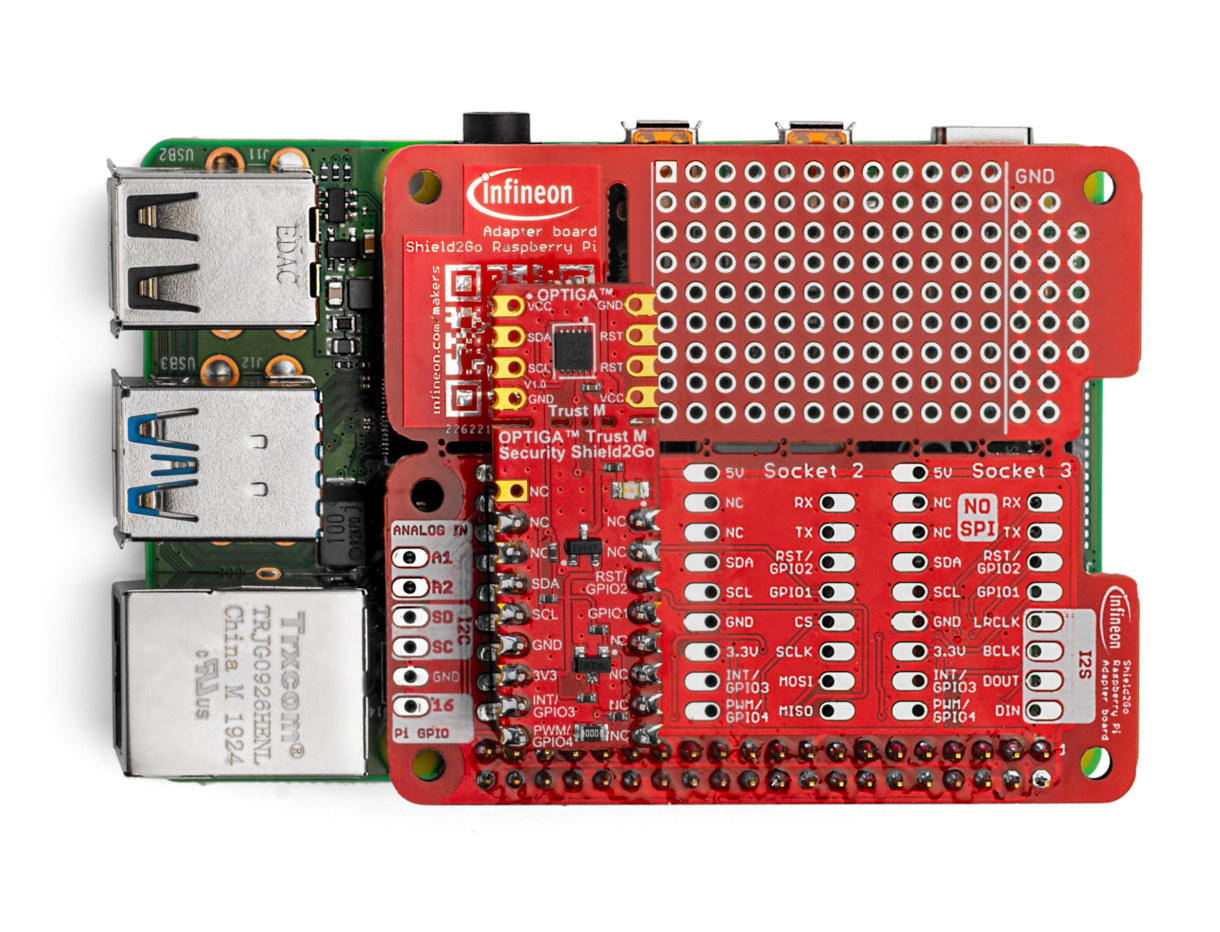
Last December, we reported that Amazon, Apple, Google, and the Zigbee Alliance had partnered to create Project Connected Home over IP (CHIP) working group with the goal of developing a royalty-free, secure Smart Home standard to increase compatibility among products over WiFi, Ethernet, Bluetooth LE, Cellular, 802.15.4 and others community protocol. Infineon has now unveiled OPTIGA Trust-M evaluation kit for Raspberry Pi designed to experiment with Connect Home over IP standard and comprised of Infineon Shield2Go HAT/adapter board, and OPTIGA Trust-M Security Shield2Go board equipped with Infineon OPTIGA Trust-M “Common Criteria Certified EAL6+” security controller. The Shield2Go adapter just re-routes the 40-pin Raspberry Pi header I/Os to sockets compatible with Infineon boards and a prototyping area. So the most important part is OPTIGA Trust-M Shield2Go which supports the following: X.509 certificates Device authentication Cryptographic support ECC NIST curves up to P-521, Brainpool r1 curve up to 512 RSA up to […]
Precursor is a mobile, open hardware, dual FPGA development kit (Crowdfunding)
Sutajio Ko-usagi PTE LTD has launched some interesting hardware on Crowd Supply over the years include Novena open-source hardware Arm laptop, and Fomu FPGA USB board. The company is now back with another project: Precursor, a mobile, open-source hardware devkit powered by not one, but two FPGA with Xilinx Spartan 7-Series FPGA, plus a super-low-power Lattice iCE40 UP5K FPGA for deep-sleep system management. The device also comes with a display, battery, and keyboard that make it looks like older Palm or Blackberry phones. Precursor FPGA devkit specifications: FPGA Xilinx XC7S50 primary System on Chip (SoC) FPGA with -L1 speed grade for longer battery life; tested with 100 MHz VexRISC-V, RV32IMAC + MMU, 4k L1 I/D cache Lattice Semi iCE40UP5K secondary Embedded Controller (EC) FPGA for power, standby, and charging functions; tested with 18 MHz VexRISC-V, RV32I, no cache System Memory – 16MB external SRAM Storage – 128MB flash Display -536 […]
Renesas Launches RA6M4 Cortex-M33 Microcontrollers for Secure IoT Applications
Arm Cortex-M33 core with Arm Trustzone security was first unveiled in 2016, and since then several silicon vendors introduced secure Cortex-M33 microcontrollers with, for instance, Nordic nRF91 LTE-IoT SoC, STMicro STM32L5 MCU family, or NXP LPC551x/S1x. Renesas has now added one more alternative with RA6M4 Cortex-M33 microcontroller family clocked at up to 200 MHz with increased performance and security compared to their earlier Cortex-M4 RA6 microcontrollers clocked at 120 Mhz. Key features for RA6M4 microcontrollers: MCU Core – Arm Cortex-M33 @ 200 MHz with TrustZone technology Memory – 256 KB RAM include 64KB ECC RAM Storage – 512-1024 embedded flash, QuadSPI, and OctaSPI memory interface Networking – Ethernet controller with DMA USB – USB 2.0 Full Speed and CAN Other Peripherals Capacitive touch sensing unit SCI (UART, Simple SPI, Simple I2C), and SPI/ I2C multi-master interface SDHI and SSI (Serial Sound Interface) Security Renesas’ Secure Crypto Engine supporting multiple symmetric […]
UPX-Edge BrainFrame Edge AI DevKit Targets Smart Video Analytics
AAEON UP Xtreme Edge (UPX-Edge) is a rugged embedded computer built around the company’s UP Xtreme SBC with a choice of 15W Whiskey Lake-U processors ranging from Celeron 4305UE to Core i7-8665UE, and optional Intel Movidius X AI accelerator cards. We previously noted the company had launched UP Xtreme Smart Surveillance kit integrating Milestone video management software (VMS) and SAIMOS video analytics software to the embedded computer. AAEON has now partnered with another company – AOTU.AI – to announce the launch of the BrainFrame Edge AI Developers Kit (DevKit) aiming to help developers and system integrators to rapidly create and deploy Smart Vision applications. The solution relies on UP Xtreme Edge mini PC fitted with an Intel Core i5-8365UE processor and 16GB RAM, 64GB eMMC flash, and two Intel Movidius Myriad X VPUs. We’ve also gone through Up Xtreme Edge specifications, so let’s instead focus on the software. This is […]
Brume-W Pocket-Sized Wireless Gateway Runs OpenWrt or Ubuntu (Crowdfunding)
GL.iNet Brume-W (GL-MV1000W) is a “pocket-sized wireless gateway for edge computing” that supports high-speed VPN up to 280Mbps with WireGuard, AdGuard ad-blocking software (AdGuard), and Tor. The device features three Gigabit Ethernet ports and built-in 2.4 GHz WiFi 4 connectivity, but it also supports Alfa AWUS036AC and AWUS036ACS USB WiFf USB dongles for users wanting dual-band WiFi 5 (AC) networking. The router ships with OpenWrt pre-installed, but also supports Ubuntu. Brume-W specifications: SoC – Marvell ARMADA 88F3720 (aka ARMADA 3720) dual-core Cortex-A53 processor @ 1.0 GHz with packet processor/network accelerator System Memory – 1GB DDR4 Storage – 16MB NOR flash and 8GB eMMC flash, MicroSD card slot up to 256GB Connectivity 3x Gigabit Ethernet ports (1x WAN + 2x LAN) Built-in 2.4 GHz 802.11b/g/n WiFi 4 up to 300 Mbps with external WiFi antennas Support for external 802.11ac WiFI 5 USB dongles USB – 1x USB host port, 1x USB-C […]
ETSI Releases EN 303 645 IoT Security Standard for Consumer Devices
To be successful over the long term, IoT must be secure, at least that’s what people say. So in 2016, UL introduced the UL 2900 IoT security standard, but it set the bar so high, that nobody ended up using it. and the UL IoT Security Rating System was introduced last year with various rankings for IoT devices security from bronze to diamond. The rating system was based on various countries/regions standard including ETSI TS 103 645 standard for the European market which defined requirements in terms of software updates, data & cryptography, logical security, system management, privacy protection, protocol security, and processes and documents. The ETSI Technical Committee on Cybersecurity (TC CYBER) has now released an update to TS 103 645 IoT security standard with ETSI EN 303 645 “that establishes a security baseline for internet-connected consumer products and provides a basis for future IoT certification schemes”. There are […]
Interview – NXP Linux BSP and Timesys Vigiles Maintenance Service & Security Updates
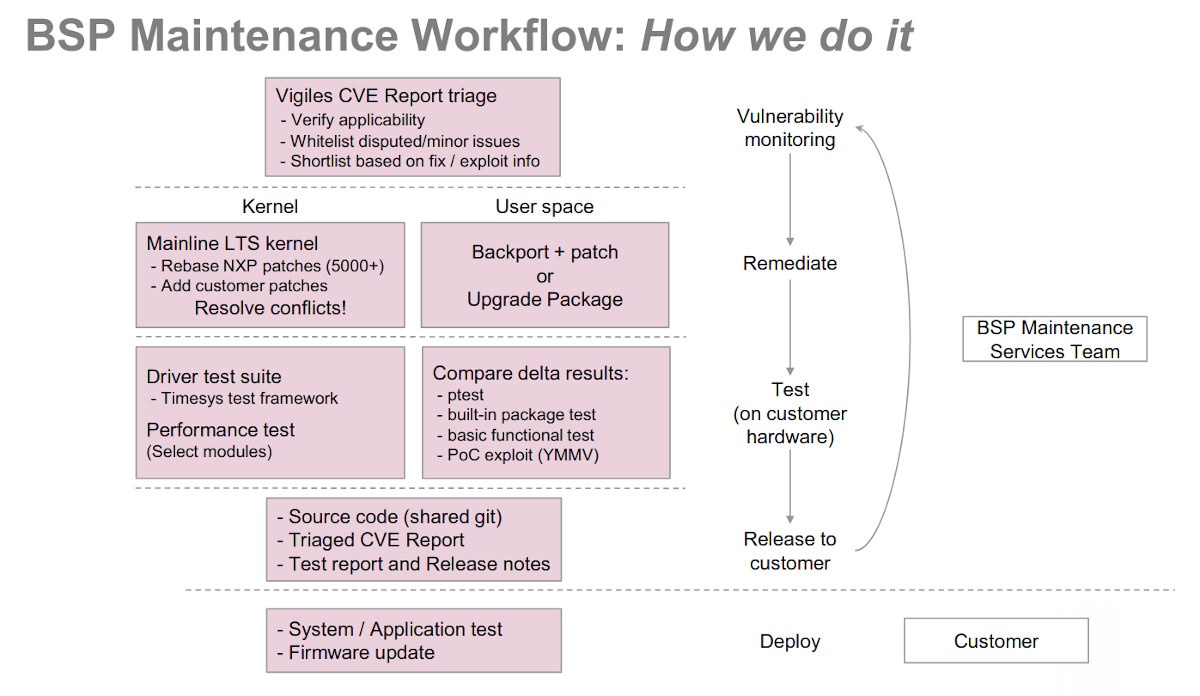
I’ve been interviewing Ed White, Manager of NXP’s Professional Support and Engineering Services, and Akshay Bhat, Director of Engineering, Security Solutions at Timesys by email to find out more about NXP Linux BSP development process, and how Timesys can help to keep it updated and secure with its Vigiles service. Q1. CNX Software readers recently discussed NXP Linux BSP update status. One person specifically noted Linux 4.14.98 used in the BSP was well over a year old, and there were various opinions about the topic, including one person suggesting NXP only provides a stable BSP and it was the ultimate responsibility of the customer to merge Linux security patchsets. Could you explain the typical development process for NXP Linux BSP, and why the company chose not to update the patchsets regularly? Answer: The kernel strategy for NXP’s i.MX family BSPs closely follows the annual cadence of kernel.org’s LTS kernel selection. […]