With Linus Torvalds taking a leave from the Linux kernel project, Greg Kroah-Hartman was the one to release Linux 4.19 last Sunday: Hi everyone! It’s been a long strange journey for this kernel release… While it was not the largest kernel release every by number of commits, it was larger than the last 3 releases, which is a non-trivial thing to do. After the original -rc1 bumps, things settled down on the code side and it looks like stuff came nicely together to make a solid kernel for everyone to use for a while. And given that this is going to be one of the “Long Term” kernels I end up maintaining for a few years, that’s good news for everyone. A small trickle of good bugfixes came in this week, showing that waiting an extra week was a wise choice. However odds are that linux-next is just bursting so […]
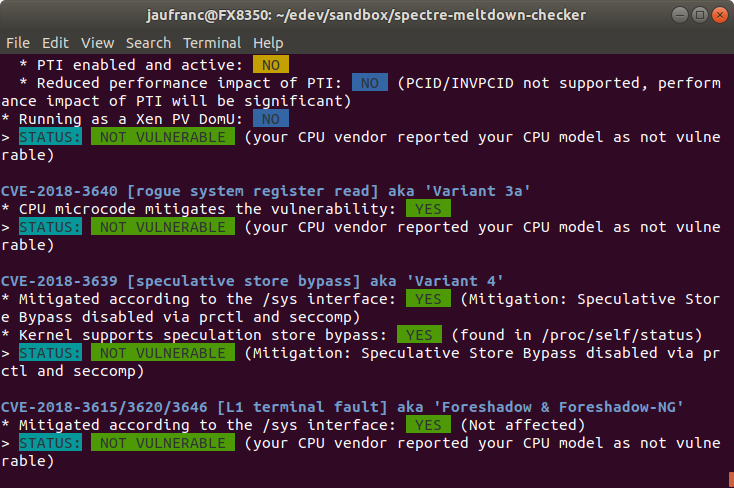
Check for Spectre, Meltdown, and L1 Terminal Fault Vulnerabilities with Spectre-meltdown-checker Script
Yesterday, we wrote a little bit about the new speculative execution vulnerability known as L1 Terminal Fault (L1TF) or Foreshadow, and a reader – MHSadri – pointed to an interesting script that checks for all three speculative execution vulnerabilities, and runs in Linux and BSD (FreeBSD, NetBSD, DragonFlyBSD) across multiple architectures: Intel x32, AMD64, Arm and ARM64. Other architectures will also work, but mitigation reporting may not be correct. So I tried it on my own machine, a computer running Ubuntu 18.04 on an AMD FX8350 processor. Installation is easy:
|
1 2 |
git clone https://github.com/speed47/spectre-meltdown-checker/ cd spectre-meltdown-checker |
The developer recommends to check the script manually first, just for security sake. You can have two way to run it: either directly inside your OS, or via docker which may be a better idea since it would not be able to mess with your system especially I had to run it with sudo to avoid permission issues. Here’s […]
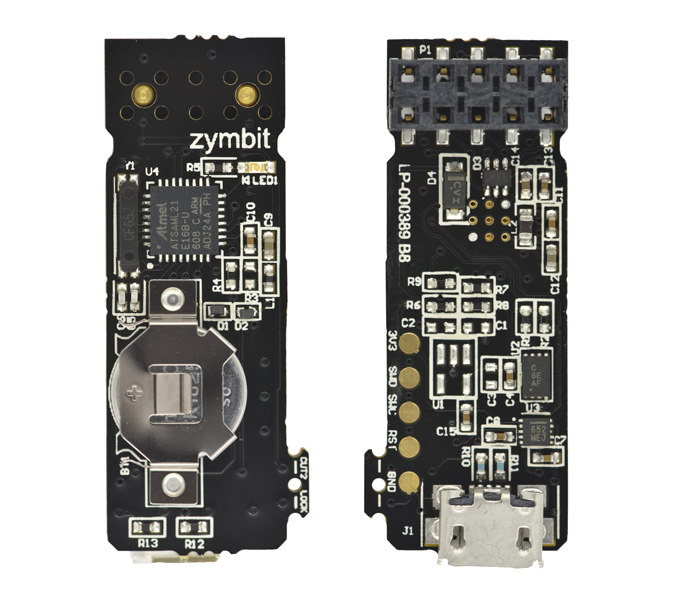
Zymkey is a Hardware Security Module for Raspberry Pi Board
Microchip ATECC508A CryptoAuthentication chip appears to be a popular way to add hardware encryption support to development boards, as we’ve seen previously with 96Boards’ Secure96 mezzanine or LoRa explorer kit, and even just earlier today with Analoglamb Fish32 Seed ESP32 education board. Another solution is from Zymbit which provides Zymkey security modules for Raspberry Pi based on the ATECC508A CryptoAuthentication chip in different form factor: either a USB stick, an I2C module, or for further integration into your own design, an SMT component. Zymkey enables multifactor device ID & authentication, data encryption & signing, key storage & generation, and physical tamper detection. It also features a secure element root of trust, a real-time clock, and a true random number generator (TRNG). The company provides a simple Python or C/C++ API to make it easier to add Zymkey support to any Linux application, and the secure module can be integrated with […]
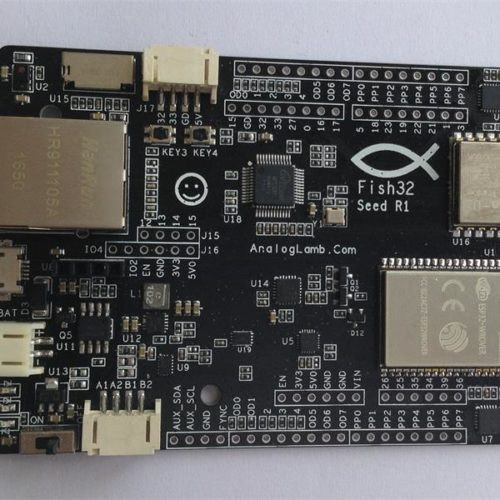
$50 Fish32 Seed “Education” ESP32 Board Comes with Plenty of I/Os, Sensors, and Connectivity Options
Sometimes I feel the word “Education” is sometimes thrown around for marketing purpose, and AnalogLamb Fish32 Seed board for “ESP32 Community Education Board” feels that way to me as so far, I could not see any tutorials or other teaching/ learning resources for the board. Having said that I can see why it could be potentially used for education: the sheer number of features, sensors, and connectivity options should allow students to learn to program my different components around ESP32. It’s just at this stage it may not be such an easy platform to learn on. Fish32 Seed board specifications: Supported ESP32 Modules – ESP32-WROVER, ALB32-WROVER, ESP32-WROOM-32 Connectivity 802.11 b/g/n WiFi and Bluetooth 4.2 via ESP32 10/100M Ethernet (RJ45) via WIZnet W5500 chip with support for up to 8 independent sockets LoRa via SX1278 chip (433 MHz) Sensors NXP MPU-9250 with 3-axis MEMS gyroscope, 3-axis MEMS accelerometer, 3-axis MEMS magnetometer […]
More Speculative Execution Exploits – Meet Foreshadow / L1 Terminal Fault
Speculative execution is a feature to speed up performance of recent processors which works by predicting and loading likely future instructions ahead of time. The features became somewhat famous a few months ago with Meltdown and Spectre vulnerabilities exploiting the features. The exploits impact Intel, AMD, Arm, and other processors to various degrees, and since the feature is built-in into the hardware, there’s no easy fix, and instead operating systems vendors, cloud service providers, hosting services and other stakeholders implemented mitigations. While a lot of progress has been made, work is still going on with the just released Linux 4.18 still getting some code changes related to the exploits. But just as solutions were found for Spectre and Meltdown, a new speculative execution exploitation has raised its ugly head: L1 Terminal Fault also known as Foreshadow. The new flaw appears to be just as serious, and a dedicated website has […]
USB Charging Actually Poses Security Risks – Hacking a Laptop via a USB-C Adapter
Smartphones have been charged over USB for many years, but with the advance of USB type-C now even laptops may be charged over USB, instead of the typical DC power barrel jack. Why am I writing about that? That’s because charging over a DC jack is normally safe, but after reading an article on BBC website, I’ve just realized when you charge over USB you also give access to the data connection, and security researcher (MG) has found a way to hack the USB-C charger of an Apple laptop and show a login prompt to steal credentials (username / password). The full details of the hack are no public, but it does require altering the hardware of the charger. So as long as you use the charger sold with your laptop, you should be safe. However, there’s always a risk if you charge from public places, or buy a charger […]
Google Titan Security Key Prevents Phishing Attacks
Phising is a social engineering method that aims to trick users into giving their passwords. This can normally be mitigated with things called “brain” and “paying attention”, but since we are all humans mistakes may happen on a bad day. Even Google employees who should be tech savvy fell for the tricks from time-to-time, so Google made employees use 2-factor authentication with a hardware security key since January 2017, and none of Google workers failed for a phising attack since then. CNET was provided with a sample of Google’s “Titan Security Key”, which comes in both USB and Bluetooth/NFC versions, and will be available for sale in Google’s online store within the next few months. The full technical details have not been provided for the key, but we do know Titan Security Keys support FIDO protocol, and are built with a secure element and a firmware written by Google that […]
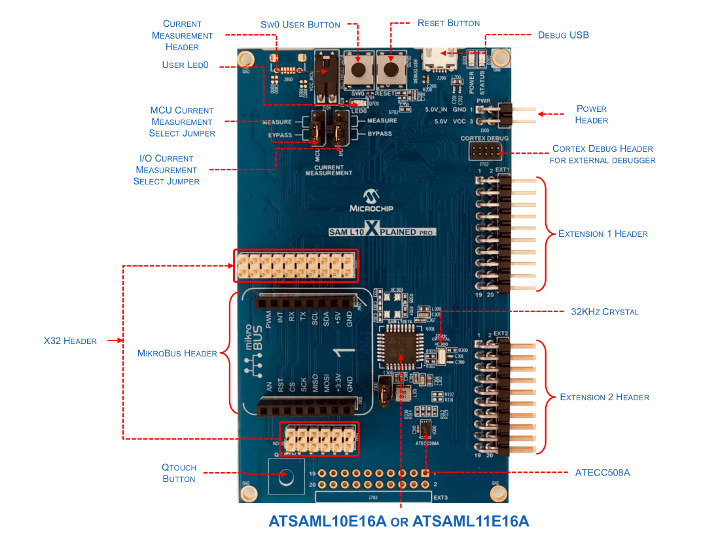
Microchip Unveils SAM L10 & SAM L11 Arm Cortex-M23 MCU Families with Arm TrustZone for Armv8-M
Microchip has recently announced new SAM L10 and SAM L11 Arm Cortex-M23 MCU families, with the SAM L11 family featuring Arm TrustZone for Armv8-M that provides hardware isolation between certified libraries, IP and application code. SAM L10 & SAM L11 MCU Families Key features: Arm Cortex M23 Core @ 32 MHz Up to 64 KB Flash and 16 KB SRAM picoPower Technology less than 25 μA/MHz in active mode less than 100 nA in sleep mode Fast wakeup time: 1.5 μS Flexible power saving features Enhanced Peripheral Touch Controller (PTC) with improved water tolerance, noise immunity and responsiveness Security (for SAM L11 only) Chip-level tamper resistance Arm TrustZone technology Secure boot Secure bootloader Crypto accelerators Secure key storage Op amp ADC and DAC Package – VQFN32, TQFP32, WLCSP32, VQFN24, SSOP24 Microchip SAM L10 MCU achieved a ULPMark score of 405, or over 200 percent better performance compared to the nearest […]