Every so often we hear about critical security vulnerabilities in the news, but new ones are actually discovered daily, so it would be nice to have some sort of search engine to find out which known security vulnerabilities a given product or processor may have before purchasing it, or even more importantly starting a project.
SAUCS does just that by having robots checking out the CVE update list, parsing the XML feed and formatting it. You can search for products or process, or subscribe to the vendors and products you want, and receive an email as soon as new changes as detected.
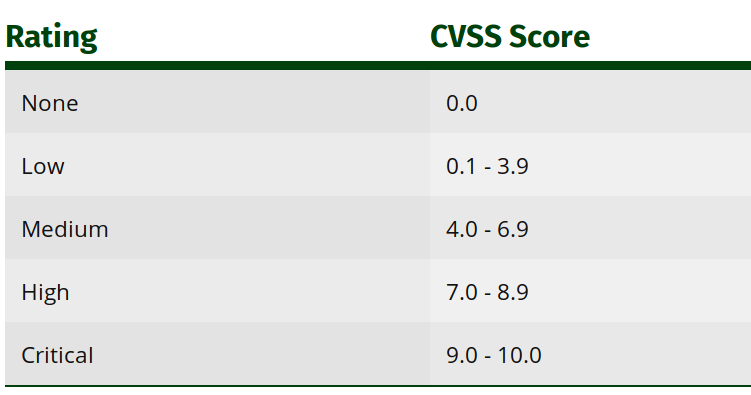
I found out about SAUCS thanks to a comment from Thomas who pointed out the Qualcomm MDM9607 processor found in Quectel EC25 LTE module had a fairly long list of CVE (Common Vulnerabilities and Exposures) entries while using the default? firmware as shown in the screenshot above. Each CVE entry is ranked by its CVSS (Common Vulnerability Scoring System) score.
It’s an interesting tool, but one should be aware of its limitations, as it’s only as good as the public information available. For example, if you search for Allwinner, you’ll find only three medium severity CVE entries, which is unlikely to reflect the reality. That means it will be most useful for search of better known products, services, or processors.
While searching for Raspberry Pi I only found one CVE entry but it is reported as being critical.
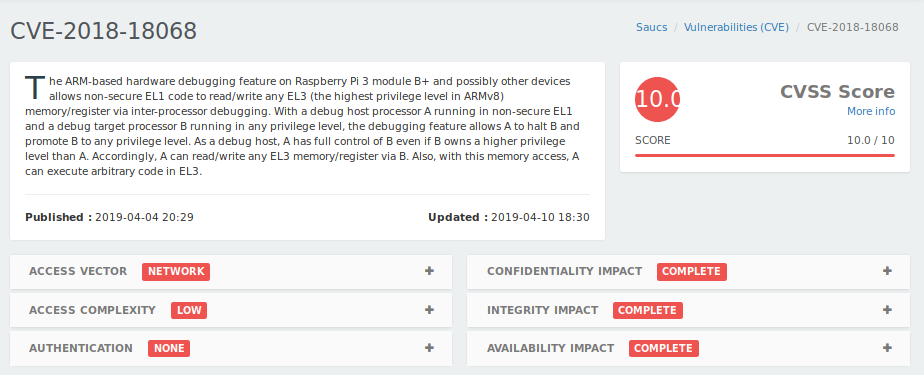
It was first published on April 04 of this year with the following description:
The ARM-based hardware debugging feature on Raspberry Pi 3 module B+ and possibly other devices allows non-secure EL1 code to read/write any EL3 (the highest privilege level in ARMv8) memory/register via inter-processor debugging. With a debug host processor A running in non-secure EL1 and a debug target processor B running in any privilege level, the debugging feature allows A to halt B and promote B to any privilege level. As a debug host, A has full control of B even if B owns a higher privilege level than A. Accordingly, A can read/write any EL3 memory/register via B. Also, with this memory access, A can execute arbitrary code in EL3.
A whitepaper entitled Understanding the security of Arm debugging features explain how to implement what they call is a NAILGUN attack. It does not only affect the Raspberry Pi 3 B+ but also other hardware like Arm Juno development board, miniNodes and Packet Arm servers based on Hauawei Kirin 620 and Cavium ThunderX respectively, and mobile devices from Google, Samsung, Xiaomi, Huawei, and Motorola. The NAILGUN attack does not rely on software bugs, so it’s an issue in Arm debugging features. There are counter-measures which can be implemented.
You can play with SAUCS yourself to find out security vulnerabilities that may affect your devices.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





Top total CVE:
Microsoft 6484
Oracle 5899
Ibm 4427
Apple 4369
Google 4159
Cisco 3942
Debian 3331
Adobe 3013
Redhat 2763
Linux 2258
Oh, sh*t. Or not?
This type of ‘statistics’ is rather useless given the many different kinds of ‘products’ the various ‘vendors’ provide.
Such vendor stuff is only interesting if you for example happen to be in the unfortunate position having to rely on network gear with known government backdoors and vulnerabilities that have to remain open due to agency requirements. Then you clearly want to monitor https://www.saucs.com/cve?vendor=cisco or even better configure notification alerts for the vendor in question 🙂
How fast they are patched is much more important than the number. Internet exposed Linux systems are under constant attack. In general the Linux based systems are quickly patched. Other vendors are not so quick with their fixes.
Considering the install base and target quality, Oracle is doing horribly while Microsoft is doing surprisingly well.
As for IBM, I’m guessing they’re issuing CVEs for their on-retainer / military systems so they mirror many Linux/Redhat, Oracle et cetra issues? Hard to explain it otherwise.