The Transport Layer Security (TLS), sometimes incorrectly referred as its predecessor: Secure Sockets Layer (SSL), helps securing messages over the network using symmetric cryptography, and optionally public-key cryptography (aka asymmetric cryptography).
This works well in servers and computers, but with the Internet of Things, even low-power sensor nodes would benefit from secure communication. The trouble is that today’s commonly-implemented RSA- and Diffie-Hellman-type public-key protocols have a memory footprint that will not fit on resource-constrained microcontrollers systems, e.g. Arm Cortex-M0 based ones, and power consumption may also be an issue since many of those are battery-powered.
I’m writing about this topic today, as there may be a better alternative for resource-constrained microcontrollers which I noticed in Arm Techcon 2019 schedule, with SecureRF Corporation’s session entitled “When it comes to connect IoT devices, how small is small?” that will present an alternative to TLS’s ECC and RSA based security that relies on in “Group Theoretic Cryptography (GTC)” designed specifically for low resource processors.
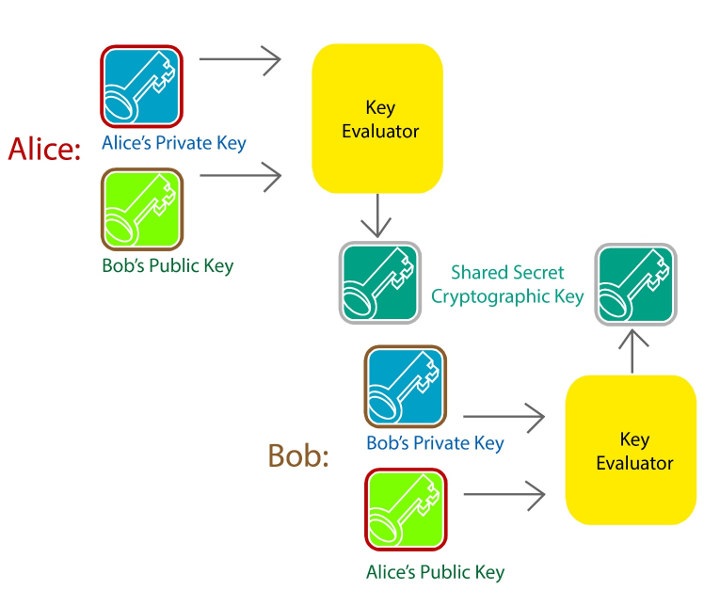 GTC is said to enable quantum-resistant drop-in replacements for ECDH and ECDSA that allow a low resource processor to securely communicate with gateway devices over an open channel. The company will showcase an Arm Cortex-M0-based MCU providing anti-counterfeiting plus data protection for a consumable item within an appliance at the event with the system transmitting analytics to its host appliance then on to a cloud server without running on top of an OS or employing TLS.
GTC is said to enable quantum-resistant drop-in replacements for ECDH and ECDSA that allow a low resource processor to securely communicate with gateway devices over an open channel. The company will showcase an Arm Cortex-M0-based MCU providing anti-counterfeiting plus data protection for a consumable item within an appliance at the event with the system transmitting analytics to its host appliance then on to a cloud server without running on top of an OS or employing TLS.
That’s all we know from the Arm Techcon presentation, but SecureRF’s website also has a page that provides highlights of the capabilities and benefits of their GTC based solutions:
- Authentication – Enables validation between devices to confirm identity. Message authentication codes and digital signatures can be used to ensure data integrity against modification or forging. This cryptographic function is used in anti-counterfeiting applications.
- Data Protection – Secures the entire data stream that is being carried, including the commands and information.
- Encryption and Decryption — A type of data protection that employs the process of obscuring information to make it unreadable without special knowledge. Encrypting the data, with a key management protocol, allows trusted users to read the data.
- Additional Security — Key agreement protocols, hash functions, and stream ciphers
The company claims GTC delivers 100 times better performance compared to other commercially available protocols. They also have a toolkits page with software and hardware security toolkits including an IoT Embedded Security SDK with pre-compiled C and assembly language routines that implement their quantum-resistant cryptographic key agreement and digital signature functions.
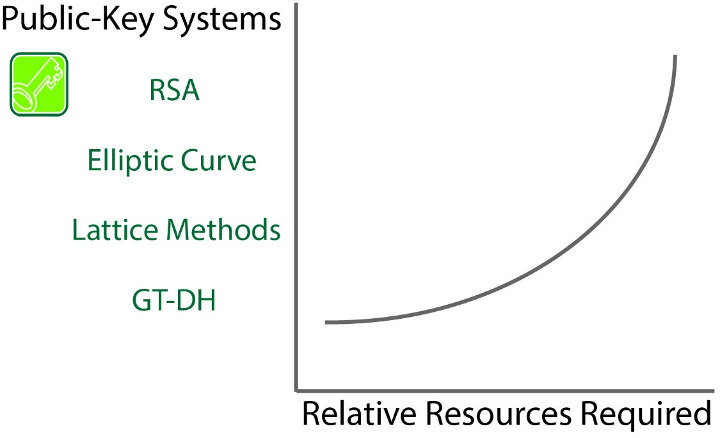
Hellman type
Apart from the simple chart above, I could not find any specific information about memory footprint or power consumption. This white paper goes into a bit more details about private and public-key cryptography, and how SecureRF GTC works:
The foundation for SecureRF’s public-key cryptosystem is based in three distinct areas of mathematics: the theory of braids; the theory of matrices with polynomial entries (expressions of finite length constructed from variables); and modular arithmetic. At its core is a highly-specialized function (replacing the standard system’s operations), known as E-Multiplication, which brings together these mathematical tools and enables the system to provide high-speed security without overwhelming the memory and available power. This core function is highly resistant to reverse engineering. Structurally, SecureRF’s public-key Group Theoretic cryptosystem is of the Diffie-Hellman type (GT-DH).
Inquiring minds may also find further details in other white papers and technical presentations.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





It will be interesting to see if this can replace expensive asymmetric crypto anywhere else. RSA is very expensive on the server side, ECDSA is very expensive on the client side. Something much cheaper on both sides would be really nice for the whole Internet’s health in general in an era where TLS was forced almost everywhere.
Love the article, this is right up my alley, thanks! I’m dubious about the security of the crypto this provides. I’d really like to see some experts take a look at it in detail before I would trust my application to it. I’ll see if Bruce Schneier says anything about it.
Found a typo: “The company will showcase an Ar, Cortex-M0” I’m guessing that’s ARM? For a second I was hoping Argon was a new code name for an M series core that had acceleration for this kind of crypto.
Yes, that was a typo.
I was really hoping it was a new processor extension. Argon goes so well with their existing Neon. 🙂
A bit confusing.
All these mathematical systems, including EC, RSA, and DH involve groups. Rings, even.
EC is on a lattice. So how is it not a ” Lattice Method”?
If we’re going to fling baffling math terms, please use them accurately. (Actually, the definitions of groups, rings, and lattices are not too complicated.)