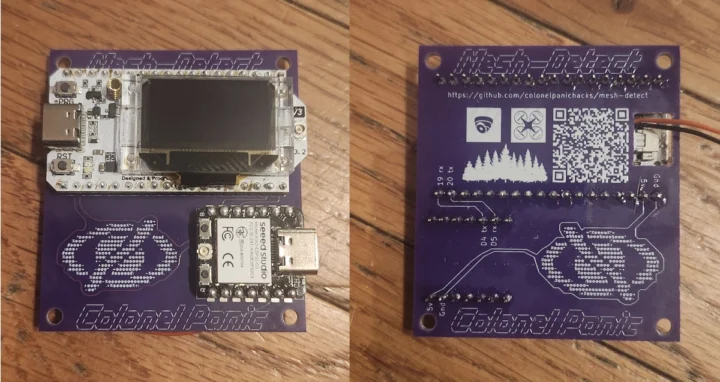
Colonel Panic’s Mesh Mapper is a project designed to map drones emitting the FAA’s Remote ID over WiFi or Bluetooth with location, altitude, pilot position, and identification data.
This project utilizes an ESP32-C3 or ESP32-S3 to capture Remote ID transmissions within range, and then feeds the data into a Python Flask web application part of Mesh Mapper that provides real-time visualization and logging. Meshtastic allows multiple detection nodes to share information across a mesh network, so several ESP32 nodes can be deployed in an area and be alerted when drones fly within your property or neighborhood.
While you could use your own ESP32-C3/S3 board and Meshtastic hardware for this project, Colonel Panic designed a breakout board for XIAO ESP32C3 or ESP32S3 WiFi & Bluetooth module and Heltec LoRa 32 V3 connected over serial to make things easier. Something like the XIAO ESP32S3 for Meshtastic & LoRa devkit might also do, but I don’t think it’s been tested with Mesh Mapper.

The ESP32 module runs the Mesh Mapper firmware for WiFi/Bluetooth Drone Remote ID forwarding to Meshtastic, and the Heltec LoRa module simply runs the Meshtastic firmware. You’ll find the firmware source code and resources to get started on GitHub.
Installing and running the Mesh Mapper server is straightforward. This is what I did on Ubuntu 24.04:
|
1 2 3 4 5 6 |
git clone https://github.com/colonelpanichacks/drone-mesh-mapper/ cd drone-mesh-mapper python3 -m venv venv source venv/bin/activate pip3 install Flask Flask-SocketIO pyserial requests urllib3 python-socketio eventlet python3 mesh-mapper.py |
Here’s the output, or the last command:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
Updated session KML: /home/jaufranc/edev/sandbox/drone-mesh-mapper/detections_20250605_100520.kml Updated cumulative KML: /home/jaufranc/edev/sandbox/drone-mesh-mapper/cumulative.kml 2025-06-05 10:05:20,320 - INFO - __main__ - No saved webhook URL file found 2025-06-05 10:05:20,320 - INFO - __main__ - Session state cleared - fresh session initialized 2025-06-05 10:05:20,321 - INFO - __main__ - Starting Drone Mapper... 2025-06-05 10:05:20,321 - INFO - __main__ - Headless mode: False 2025-06-05 10:05:20,321 - INFO - __main__ - Auto-start enabled: True 2025-06-05 10:05:20,321 - INFO - __main__ - Port monitoring interval: 10s 2025-06-05 10:05:20,321 - INFO - __main__ - === DRONE MAPPER STARTUP === 2025-06-05 10:05:20,321 - INFO - __main__ - Loading previously saved ports... 2025-06-05 10:05:20,321 - INFO - __main__ - Loading previously saved webhook URL... 2025-06-05 10:05:20,321 - INFO - __main__ - No previously saved ports found. 2025-06-05 10:05:20,321 - INFO - __main__ - Starting port monitoring thread... 2025-06-05 10:05:20,321 - INFO - __main__ - Port monitoring thread started 2025-06-05 10:05:20,322 - INFO - __main__ - WebSocket broadcaster thread started 2025-06-05 10:05:20,322 - INFO - __main__ - === STARTUP COMPLETE === 2025-06-05 10:05:20,322 - INFO - __main__ - Cleanup timer started 2025-06-05 10:05:20,322 - INFO - __main__ - Starting web interface on port 5000 2025-06-05 10:05:20,322 - INFO - __main__ - Access the interface at: http://localhost:5000 2025-06-05 10:05:20,326 - INFO - __main__ - Port availability changed. Current ports: {'/dev/ttyS8', '/dev/ttyS10', '/dev/ttyS25', '/dev/ttyS1', '/dev/ttyS29', '/dev/ttyS14', '/dev/ttyS20', '/dev/ttyS11', '/dev/ttyS2', '/dev/ttyS31', '/dev/ttyS13', '/dev/ttyS15', '/dev/ttyS26', '/dev/ttyS17', '/dev/ttyS9', '/dev/ttyS22', '/dev/ttyS12', '/dev/ttyS18', '/dev/ttyS7', '/dev/ttyS30', '/dev/ttyS6', '/dev/ttyS27', '/dev/ttyS23', '/dev/ttyS21', '/dev/ttyS19', '/dev/ttyS4', '/dev/ttyS16', '/dev/ttyS28', '/dev/ttyS24', '/dev/ttyS0', '/dev/ttyS5', '/dev/ttyS3'} |
We’re told the web interface can be accessed at http://localhost:5000, so let’s do that:
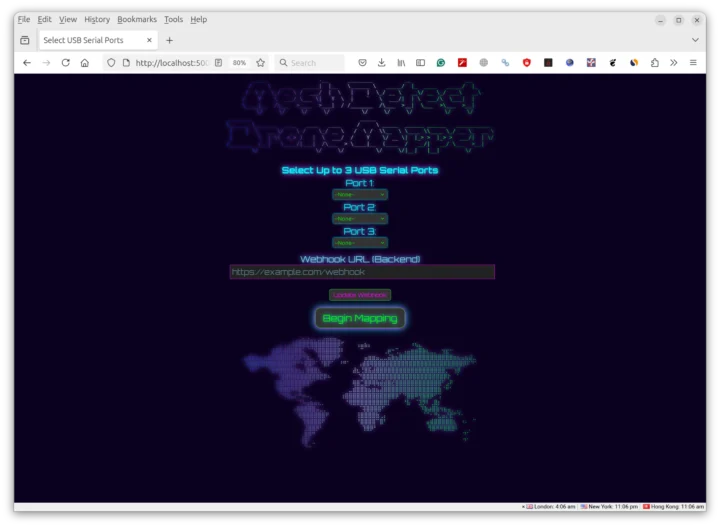 If you don’t have the hardware on hand, you can simulate drones with the “Arizona Desert Test Suite” in mapper_test. Let’s try that:
If you don’t have the hardware on hand, you can simulate drones with the “Arizona Desert Test Suite” in mapper_test. Let’s try that:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 |
(venv) jaufranc@CNX-LAPTOP-5:~/edev/sandbox/drone-mesh-mapper/mapper_test$ python3 mapper_test.py Initialized Desert Eagle (MAC: AA:BB:CC:DD:EE:01) at lat 33.540246, lng -111.792698 Initialized Cactus Hawk (MAC: AA:BB:CC:DD:EE:02) at lat 33.617131, lng -112.015625 Initialized Saguaro Scout (MAC: AA:BB:CC:DD:EE:03) at lat 33.587863, lng -112.063868 Initialized Mesa Phantom (MAC: AA:BB:CC:DD:EE:04) at lat 33.684548, lng -111.828421 Initialized Sonoran Surveyor (MAC: AA:BB:CC:DD:EE:05) at lat 33.363335, lng -111.948921 ============================================================ ARIZONA DESERT DRONE TEST CONFIGURATION ============================================================ Test Area: Arizona Sonoran Desert Center: 33.494200, -111.926100 Bounds: N33.700 S33.300 E-111.700 W-112.200 Area Size: ~50km x 50km Drone 1: Desert Eagle MAC: AA:BB:CC:DD:EE:01 Basic ID: AZTEST001 Start Position: 33.540246, -111.792698 Pilot Position: 33.510668, -111.798463 Flight Pattern: circular FAA Registration: DJI Phantom 4 Drone 2: Cactus Hawk MAC: AA:BB:CC:DD:EE:02 Basic ID: AZTEST002 Start Position: 33.617131, -112.015625 Pilot Position: 33.599272, -112.022477 Flight Pattern: circular FAA Registration: Skydio Air 2S Drone 3: Saguaro Scout MAC: AA:BB:CC:DD:EE:03 Basic ID: AZTEST003 Start Position: 33.587863, -112.063868 Pilot Position: 33.553873, -112.032204 Flight Pattern: search_pattern FAA Registration: Parrot ANAFI Drone 4: Mesa Phantom MAC: AA:BB:CC:DD:EE:04 Basic ID: AZTEST004 Start Position: 33.684548, -111.828421 Pilot Position: 33.700000, -111.789722 Flight Pattern: linear FAA Registration: Yuneec Phantom 4 Drone 5: Sonoran Surveyor MAC: AA:BB:CC:DD:EE:05 Basic ID: AZTEST005 Start Position: 33.363335, -111.948921 Pilot Position: 33.319650, -111.935694 Flight Pattern: circular FAA Registration: Skydio Phantom 4 ✓ Successfully connected to mesh-mapper at http://localhost:5000 🏜️ Starting Arizona Desert Drone Simulation Duration: 30 minutes Update interval: 2.0 seconds Test area: {'north': 33.7, 'south': 33.3, 'east': -111.7, 'west': -112.2} Number of drones: 5 ============================================================ Started simulation thread for Desert Eagle Started simulation thread for Cactus Hawk Started simulation thread for Saguaro Scout Started simulation thread for Sonoran Surveyor Started simulation thread for Mesa Phantom 🛩️ Desert Eagle: lat 33.497462, lng -111.916647, alt 158.9m, RSSI -50.2dBm 🛩️ Cactus Hawk: lat 33.502284, lng -111.931986, alt 358.1m, RSSI -52.5dBm 🛩️ Saguaro Scout: lat 33.587862, lng -112.063868, alt 296.6m, RSSI -45.6dBm 🛩️ Mesa Phantom: lat 33.684547, lng -111.828422, alt 152.3m, RSSI -47.1dBm 🛩️ Sonoran Surveyor: lat 33.484349, lng -111.927819, alt 270.4m, RSSI -56.7dBm 🛩️ Desert Eagle: lat 33.497318, lng -111.916599, alt 157.0m, RSSI -47.2dBm |
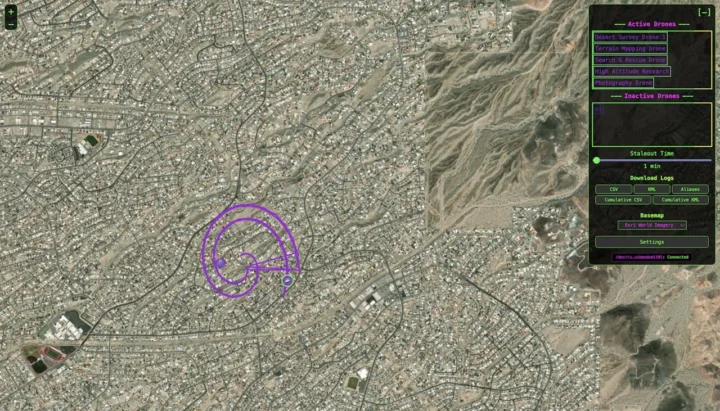
Now we can see five drones in the web interface with location updated in real-time.
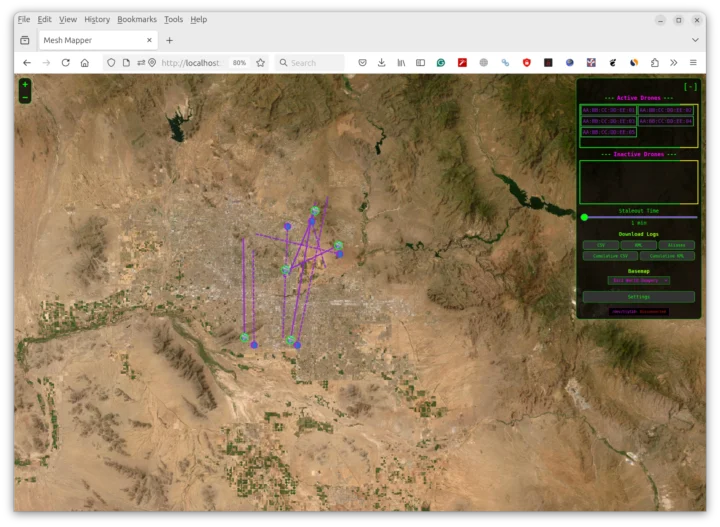 The MAC addresses of the drones are shown in the simulation, but you can create aliases to show more user-friendly names. Colonel Panic also shared more detailed instructions and some screenshots on Hackster.io. So let’s have a quick look.
The MAC addresses of the drones are shown in the simulation, but you can create aliases to show more user-friendly names. Colonel Panic also shared more detailed instructions and some screenshots on Hackster.io. So let’s have a quick look.
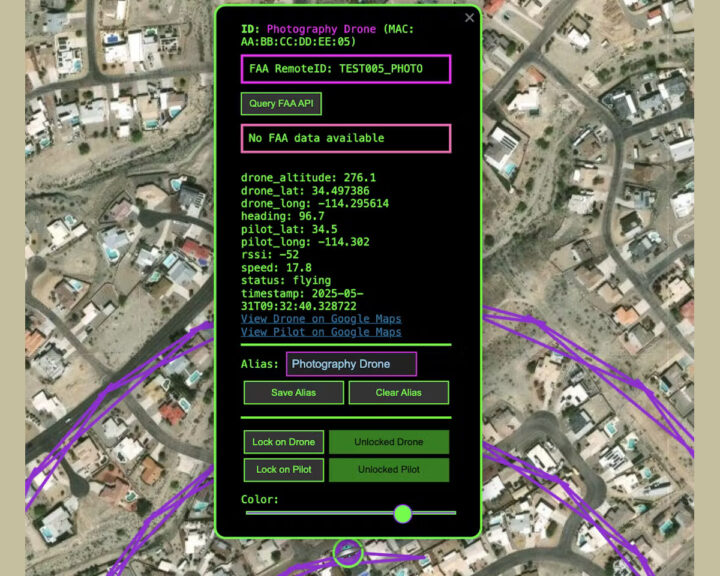
The screenshot above shows a map with five drones from the simulation, and the one below zooms in and reveals details about one of the drones and its pilot.
Testing with actual hardware has shown detection ranges of 5 kilometers in urban environments and 10 to 15 kilometers in open areas with good antennas and overlapping coverage that eliminates dead zones when using multiple devices.
The project can be useful for education, research, privacy protection, and personal security: Monitor activity around sensitive locations like your home or business. If you’d like to use the Mesh Detect hardware for the project, the breakout board is sold on Tindie for $15, and a fully assembled kit for $100.
I’ve also embedded an FAA video about Remote ID, and based on the comments on YouTube, it applies to most civilian drones. Many people are not too happy about it due to privacy concerns and because existing drones need to be retrofitted with a Remote ID module, adding to their weight. Note that it’s not specific to the US, as the European Union has its own Remote ID rules as well as some other countries like Japan, Australia, etc…

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.