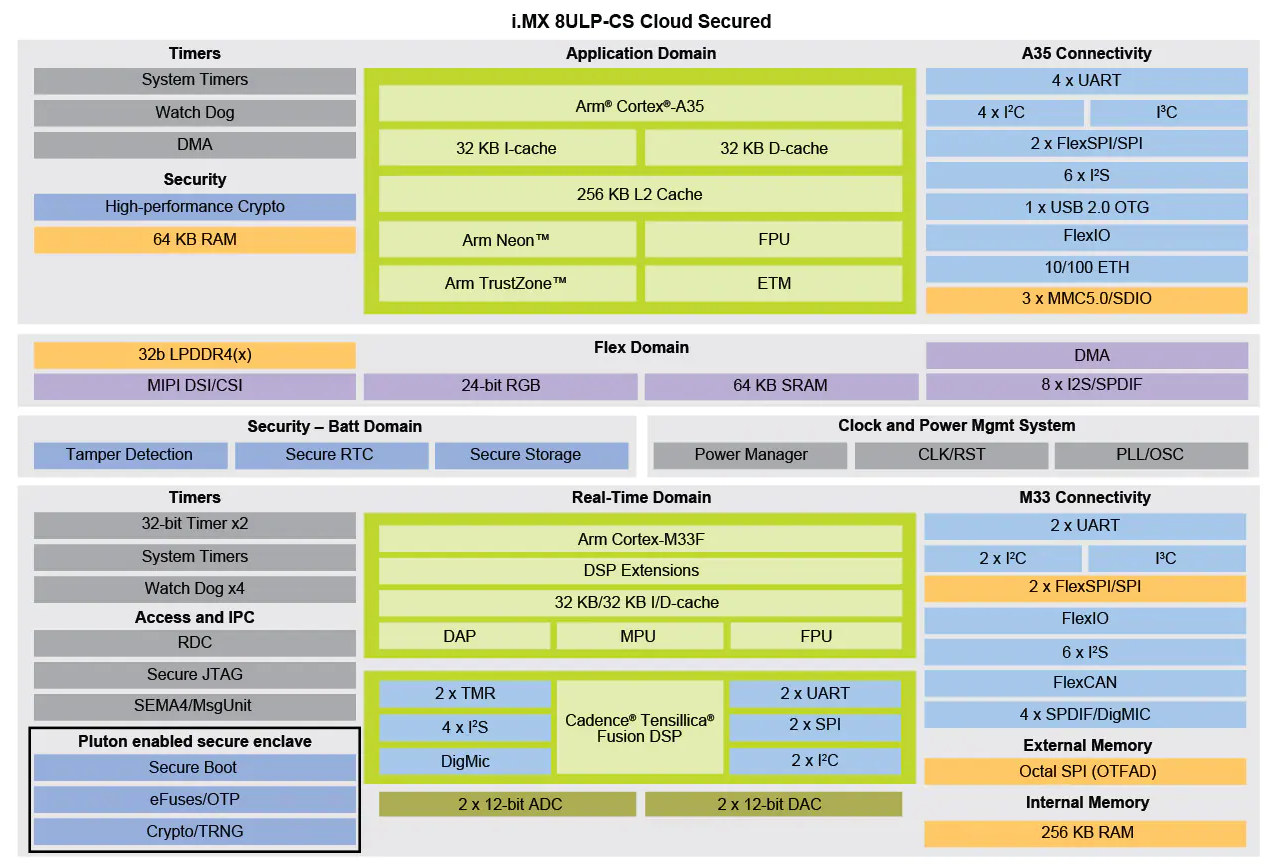
NXP may have just unveiled plans for i.MX 9 processor family with Arm Ethos U65 microNPU, and advanced security using the company’s EdgeLock enclave, but NXP also introduced new members to its popular i.MX 8 series with i.MX 8ULP and i.MX 8ULP-CS (Cloud Secured) processors. Both processors come with a mix of Cortex-A35 application processor(s) and Cortex-M33 real-time core, as well as Energy Flex low-power architecture and EdgeLock secure enclave, but i.MX 8ULP-CS includes Microsoft Pluton for secure cloud connectivity and lacks 2D/3D graphics and the HiFi 4 audio DSP. NXP i.MX 8ULP and 8ULP-CS key features and specifications: CPU i.MX 8ULP – Up to two Arm Cortex-A35 @ 1.0 GHz and Arm Cortex-M33 @ 216 MHz, i.MX 8ULP-CS – One Arm Cortex-A35 @ 1.0 GHz and Arm Cortex-M33 @ 216 MHz GPU (i.MX 8ULP only) – 2D GPU, and 3D GPU with support for OpenGL ES 3.1, OpenCLTM, Vulkan […]
ANNKE CZ400 AI security camera review – Part 1: Specs, unboxing and teardown
We’re starting to see more and more security cameras with built-in AI features such as Reolink RLC-810A 4K camera with people & vehicle detection or the lower cost Vacom Cam Full HD camera with person detection only, which I have not reviewed yet due to some technical issues. I would not buy a camera without AI now as such features greatly reduce false positives. Another model has now come my way with ANNKE CZ400 (aka I91BK) 2K security camera that comes with even more advanced AI-accelerated computer vision features with not only face detection, but also intrusion detection, line crossing detection, region entrance detection, region exiting detection, object removal detection, unattended baggage detection, and audio exception detection. In this first part of the review, we’ll check the specifications, the content of the package with an unboxing, as well as a partial teardown that is needed to install a microSD card. […]
NXP i.MX 9 processors to integrate Arm Ethos U-65 microNPU, EdgeLock secure enclave
NXP i.MX 6 and i.MX 8 processors are widely used in industrial boards and systems-on-module, and the company has now teased a new family with i.MX 9 processors integrating Arm Ethos-U65 1 TOPS microNPU, as well as the company’s EdgeLock secure enclave for increased security. The company did not provide that many technical details, so we still don’t know which CPU cores, GPU, and exact peripherals will be found in the processor. But we do know the i.MX 9 processors will be manufactured with a 16/12nm FinFET class of process technology optimized for low power, and features the “Energy Flex” architecture that combines “heterogeneous domain processing (independent applications processor and real-time domains with a separate low-power multi-media domain), design techniques, and process technology to maximize performance efficiency”. That means most blocks of the processor can be turned off for low power audio or CAN networking use cases, and other industrial […]
STM32U5 Cortex-M33 MCU gets more performance, 2D graphics accelerator, and advanced security
The first STM32 MCU based on Arm Cortex-M33 core was the ultra-low-power STM32L5 microcontroller, and the company is now following up with the STM32U5 series also designed for smart applications including wearables, personal medical devices, home automation, and industrial sensors. The new family has a higher 160 MHz clock speed, up to 2048 KB flash, up to 786 KB RAM, a 2D graphics accelerator, several peripherals have been upgraded, and a new autonomous mode lets DMA and peripherals keep working while most of the device sleeps in order to save power. STM32U5 MCUs also integrate additional hardware security features, and are manufactured using a 40nm process, which the company says is the most advanced process suitable for microcontrollers. Just like for the STM32L5 family, there are two product lines in the STM32U5 series which mostly differ in their security features: STM32U575 with 1024 to 2048 KB of flash memory, 786 […]
Android 12 developer preview released – What’s New?
Google releases a new version of Android every year, and the company is now usually releasing a developer preview in February to allow feedback and testing from app developers. So here we are with the Android 12 developer preview having just been released by Google with changes ranging from trust and safety to media transcoding to support for AVIF image format. Android 12 highlights: Performance Improved Binder IPC calls – Google engineers have had a look at latency and workload distribution, and made optimizations that reduce the median experience. This has yielded roughly a 2x performance increase on Binder calls overall, and up to a 47x improvement in refContentProvider(), 15x in releaseWakeLock(), and 7.9x in JobScheduler.schedule(). Foreground service optimizations – To ensure a better experience for users, foreground service starts from the background will be blocked for apps that are targeting the new platform. Android 12 will also delay the […]
Linux 5.11 Release – Main Changes, Arm, MIPS & RISC-V Architectures
Linus Torvalds has released Linux 5.11 just in time for… “Valentine’s Day”: Nothing unexpected or particularly scary happened this week, so here we are – with 5.11 tagged and pushed out. In fact, it’s a smaller-than-average set of commits from rc7 to final, which makes me happy. And I already have several pull requests lined up for tomorrow, so we’re all set for the merge window to start. But in the meantime – and yes, I know it’s Valentine’s Day here in the US – maybe give this release a good testing before you go back and play with development kernels. All right? Because I’m sure your SO will understand. Linus Last time around, Linux 5.10 was an LTS release that added EXT-4 performance enhancements, improved post-Spectre performance, as well as the enablement of BCM2711 (Raspberry Pi 4) display pipeline, among other many changes. Some of the notable changes in […]
Vacos Cam AI Security Camera Review – Part 1: Specifications, Unboxing and Teardown
As we’ve seen in our Reolink RLC-810A review, AI security cameras greatly reduce the number of false alerts generated by motion sensors, and the Reolink 4K security camera we tested was capable of people and vehicle detection. The Reolink model does not support WiFi, so I had to run a long Ethernet cable, plus a power extension to connect a 12V power adapter since I don’t own a PoE injector. But I’ve been given the opportunity to review another AI security camera, namely Vacos Cam, that also supports human detection, but relies on WiFi connectivity and can be powered by a solar panel removing the need for potentially long cable. As a bonus, it comes with eMMC for storage, so there’s no need for a MicroSD card. In the first part of the review, I’ll list the specifications, unbox the power panel and camera, and tear down Vacos Cam to […]
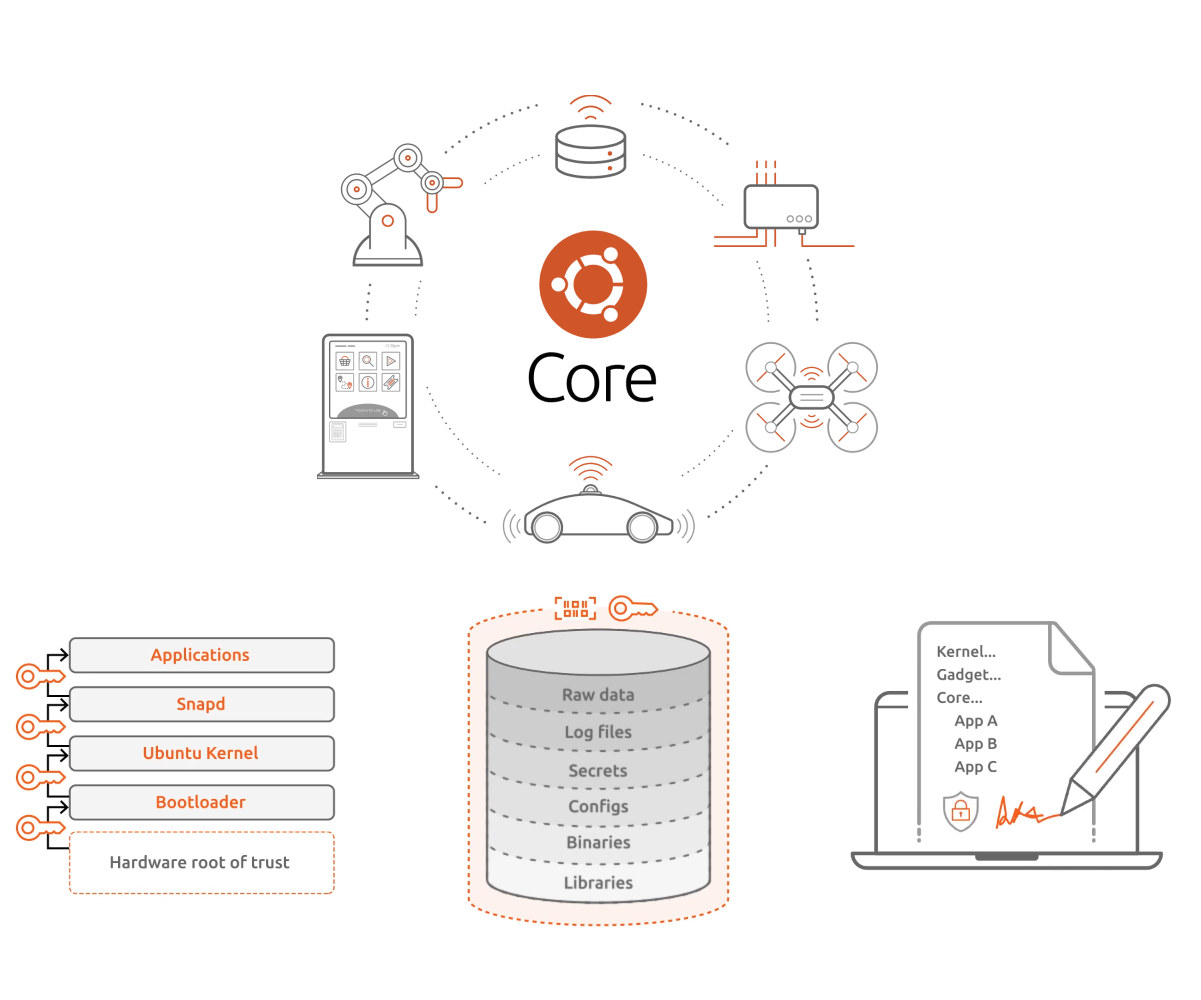
Ubuntu Core 20 released for secure Linux IoT devices and embedded systems
Canonical has just released Ubuntu Core 20, a minimal, containerized version of Ubuntu 20.04 LTS for IoT devices and embedded systems. The company highlights several security improvements and features of the new version of the Linux-based operating system with secure boot, full disk encryption, secure device recovery, and secure containers. Ubuntu Core 20 is said to come with all benefits from Ubuntu 20.04 LTS such as regular, automated updates, the ability to manage custom app stores, and offers a longer 10-year support window. Ubuntu Core is available and certified on popular32-bit and 64-bit x86 and Arm single board computers such as Intel NUC or Raspberry Pi 4. Minimum requirements include a single-core processor @ 500 MHz, 256MB RAM, and 512MB storage. Alternatively, it’s also possible to run it in a virtual machine on your PC. Security is further enhanced with apps running in containers, and since only the necessary software […]