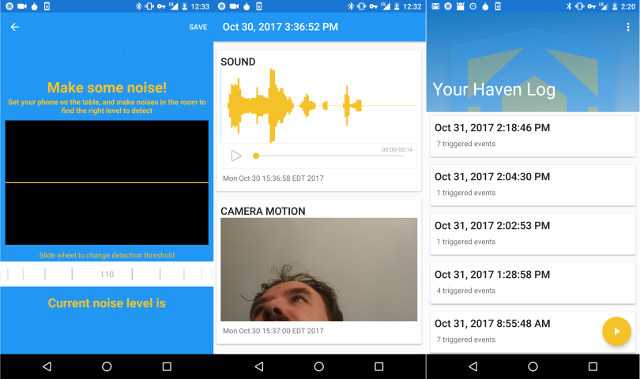
About two years ago, I wrote a post asking what to do with old devices instead of throwing them away. My own proposals included giving them away, reselling them on eBay, recycling them for other purpose like servers or download clients, or scavenging some parts. Other people also comments what they did with theirs, for example setting up a Linux cluster with old TV boxes. Another way to recycling an old (Android) smartphone – albeit you could always buy an inexpensive one – is to install and run Haven, an open source app that transforms your phone into some sort of smart security camera, but instead of only using the camera from the phone, the app also logs audio events using its microphone (array), as well as data reported by sensors. One of you first reaction might be: “cool! somebody may an app that would allow hackers or government to […]
Fingbox Helps You Monitor & Manage Devices on Your Network with Your iOS/Android Smartphone
Fing network scanner mobile app available for iOS and Android that allows you to discover which devices are connected to your Wi-Fi network, map devices, detect intruders, assess network security risks, troubleshoot network problems, and optimize wireless network performance. But in order to go beyond network monitoring, the developers have designed Ubuntu Core based Fingbox hardware to add features such as access control (e.g. parental control), analyze the usage of bandwidth for each clients, find Wi-Fi sweet spots/ avoid black spots, verify your Internet speed, monitor devices in your network, and protects it with a digital fence that works against threats. From a hardware perspective Fingbox is a round shaped Ethernet node with the following specifications: Processor – ARMv7 processor System Memory – 1GB RAM Connectivity – Gigabit Ethernet The Linux (Ubuntu Core) device just needs to be connected to your network via an Ethernet cable, and powered by its […]
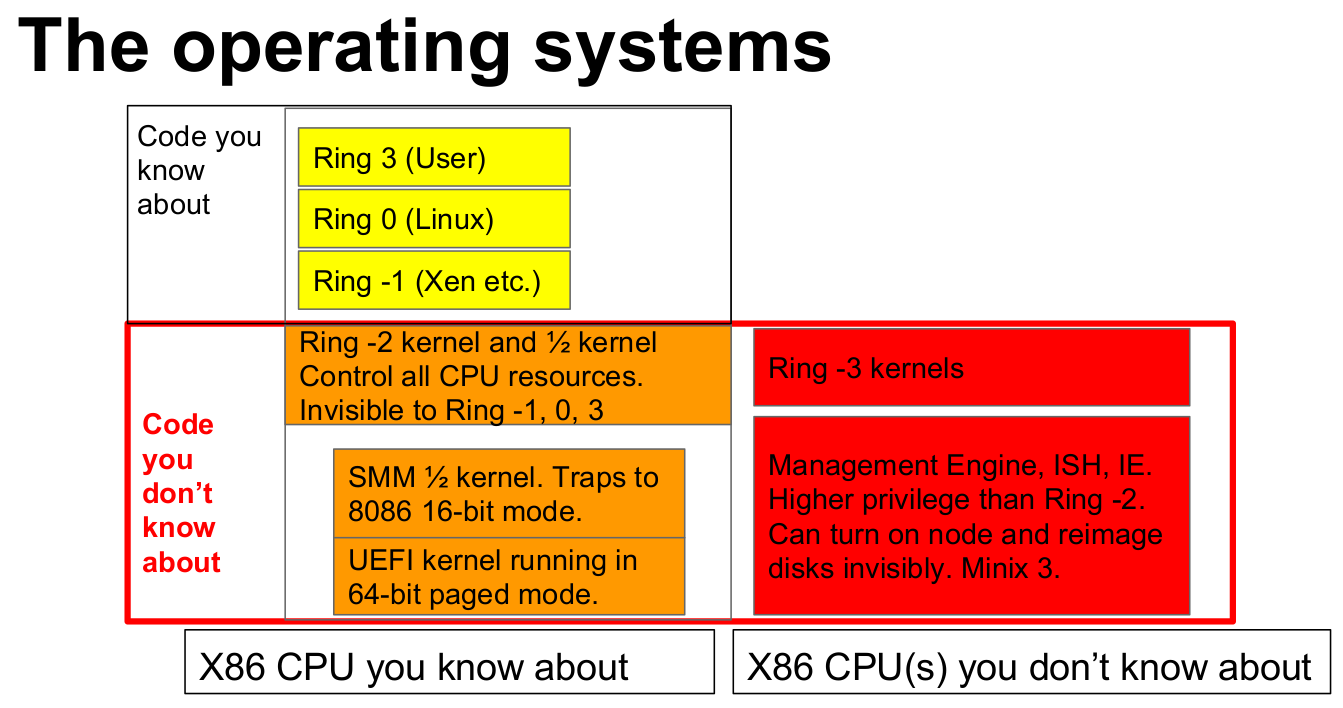
MINIX based Intel Management Engine Firmware & UEFI are Closed Source & Insecure, NERF to the Rescue!
You may have heard a few things about Intel Management Engine in recent months, especially as security issues have been found, the firmware is not easily upgradeable, and the EFF deemed it a security hazard asking Intel for ways to disable it. In recent days, I’ve seen several media reports about the Management Engine being based on an Intel Quark x86-based 32-bit CPU running MINIX open-source operating system. Keep in mind, there’s nothing nefarious about MINIX, it’s just that Intel keeps its own developments on top closed. One of sources for the information is a blog post explaining how to disable Intel ME 11, but ZDNET also points to one of the talks at the Embedded Linux Conference Europe 2017 entitled “Replace Your Exploit-Ridden Firmware with Linux” by Ronald Minnich, Google which explains the problem, and proposes a solution to (almost) disable Intel’s ME, and replace UEFI by a small […]
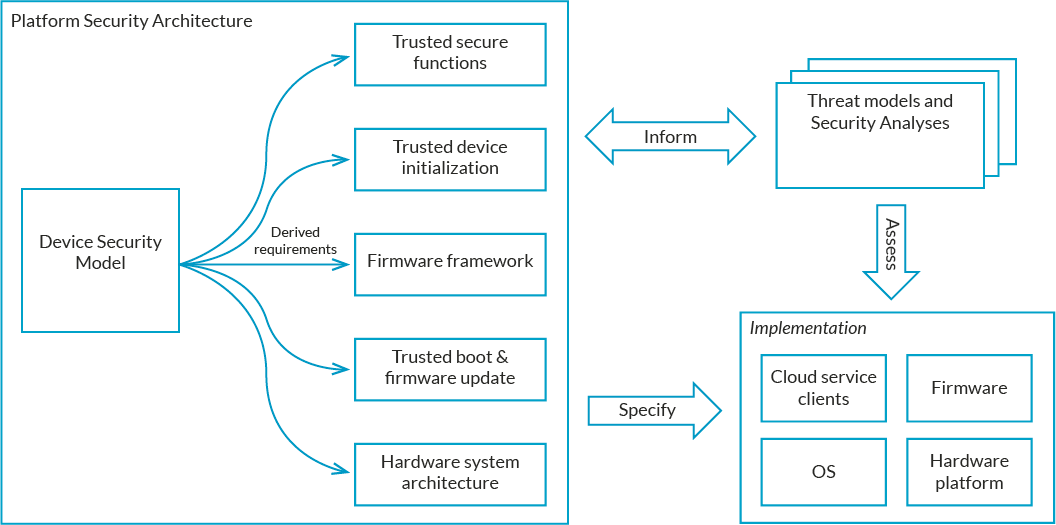
Arm’s Platform Security Architecture Aims to Secure the Internet of Things (IoT)
News are published nearly everyday about a security breach or flaw in IoT devices, and last year, Softbank CEO, and new Arm owner, Masayoshi Son explained that to reach his goal of one trillion IoT devices and singularity, security had to be addressed, as everything was currently too easily hackable, including cars equipped with lots of electronics but very weak security. As Arm Techcon 2017 is underway, the company has been working on improving IoT security and announced the Platform Security Architecture (PSA) designed for low cost IoT devices. PSA has three major components: Threat Models and Security Analyses derived from a range of typical IoT use cases. Architecture specifications for firmware and hardware. An open source project, similar to Arm Trusted Firmware for mobile clients. PSA is designed for low cost IoT devices, which would have not the resources (processing power, memory, battery power…) to run a full Trusted […]
Samsung IoT Security News – ARTIK Secure IoT Modules, SmartThings Cloud, and Secure Element
Samsung has made several announcements with IoT, especially IoT security. First, Samsung ARTIK 053, ARTIK 530 and ARTIK 710 modules are getting an “s” version, which stands for “robust security”, as well as a new ARTIK 055s module, and all ARTIK modules can now work with SmartThings Cloud uniting the company’s existing services – ARTIK Cloud and Samsung Connect Cloud – into a single IoT platform. Separately, the company announced their Secure Element solution which combines eFlash memory and new security software. Samsung ARTIK “s” modules & ARTIK 055s The company explains in their blog that ARTIK 053s, 530s, 710s, and the all new 055s will feature “advanced protection, integrated cloud services, and hosted security services with “enhanced ARTIK end-to-end security by providing greater protection for IoT data as well as prevention against hacking”. The press release is a little more specific: ARTIK secure IoT modules provide a strong root […]
Geolocation on ESP8266 without GPS Module, only WiFi
When I think about geolocation in I normally think about global navigation satellite systems such as GPS, GLONASS, Galileo, or Beidou, as well as IP geolocation, but the latter is highly inaccurate, and often only good for find out about the country, region, or city. But if you’ve ever been into your phone location settings, you’d know GPS is only one option, as it can also leverage cellular base stations and WiFi SSIDs, where the former working where there’s coverage, and the later in area with a high enough density of access points. Somehow, I had never thought about using such technology to find location with WiFi modules until Espressif Systems released an application note entitled “Geolocating with ESP8266“. This document describes how the ESP8266 module may be used to scan for nearby Wi-Fi access points and, then, use their SSID, RSSI and MAC address to obtain a potential fix […]
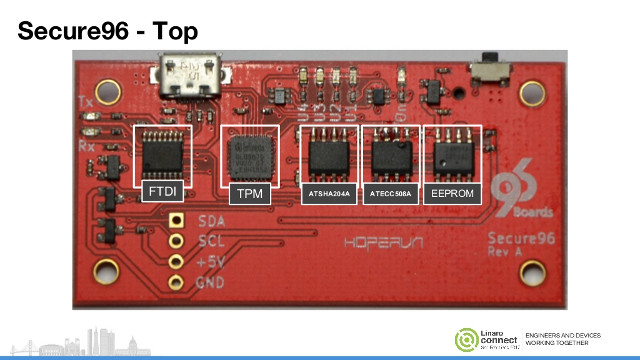
Secure96 is a 96Boards Mezzanine Expansion Board To Experiment with Hardware Based Security
With the Internet of things booming and taking a more important role in our lives, security will become more and more critical. So far, it has often been an afterthought with modems & routers frequently shipping with default username and password, and getting security right is really hard, as shown by the recent CLKSCREW attack that somehow leverages DVFS to break ARM TrustZone security, and that “is not a software bug, nor a hardware bug, it’s a fundamental part of the energy management design”, so most ARM platforms are vulnerable. Optimal security normally combines software and hardware, so having a platform to experiment with different HW security solutions would be useful, and that’s what Secure96 Mezzanine board for 96Boards aims for. Secure96 expansion board specifications: Security ICs Microchip Atmel ATSHA204A SHA-based CryptoAuthentication crypto element device Microchip Atmel ATECC508A crypto device with ECDH (Elliptic Curve Diffie–Hellman) key agreement Infineon SLB 9670 TPM […]
Linaro Connect SF 2017 Welcome Keynote – New Members, Achievements, the Future of Open Source, and More…
Linaro Connect San Francisco 2017 is now taking place until September 29, and it all started yesterday with the Welcome Keynote by George Grey, Linaro CEO discussing the various achievements since the last Linaro Connect in Budapest, and providing an insight to the future work to be done by the organization. The video is available on YouTube (embedded below), and since I watched it, I’ll provide a summary of what was discussed: Welcoming New Members – Kylin (China developed FreeBSD operating systems) joined LEG (Enterprise Group), NXP added LHG (Home Group) membership, and Xilinx joined LITE (IoT and Embedded). Achievements OPTEE open portable trusted environment execution more commonly integrated into products. Details at optee.org. LEG 17.08 ERP release based on Linux 4.12, Debian 8.9 with UEFI, ACPI, DPDK, Bigtop, Hadoop, etc… LITE group has been involved in Zephyr 1.9 release, notably contributing to LwM2M stack More projects to be found […]