Transport Layer Security (TLS) is the protocol that allows for secure websites (via https), and currently, TLS 1.2 is the version most commonly used today, with 1.0 and 1.1 still supported by many servers for backward compatibility with older browsers, including the one running this blog. TLS 1.3 is the next version, already supported in libraries and server software such as wolfSSL or nginx, and promises to be more efficient – important for battery operated devices (IoT) – thanks to features like zero-RTT (0-RTT) mode, speedy with a restructured handshake state machine, and more secure.
However, changes in security protocol may mess up connection with some browsers or middleboxes, as I experience when I enabled https on CNX Software using Let’s Encrypt with nginx and Cloudflare, with around 0.5% of users losing access due to using older web browsers and operating systems such as Internet Explorer on Windows XP. According to Cloudflare, compatibilities issues are the main reasons why TLS 1.3 has not been enabled in web browsers, since around 3% of traffic fails when TLS 1.3 is enabled, mostly due to incorrect implementation of TLS version negotiations in some middleboxes.
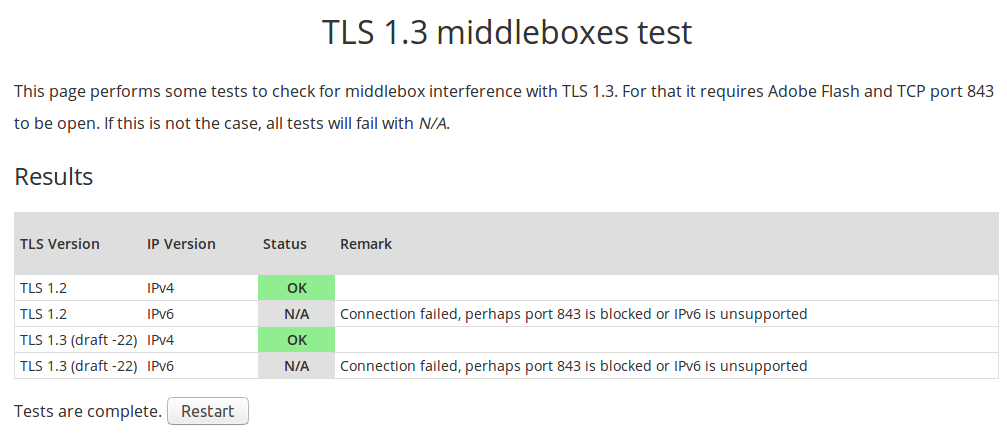
TLS 1.3 draft 22 improves compatibility by making TLS 1.3 look like TLS 1.2 to those middleboxes, and success rates have increased to 98+%, but more testing is needed. You can help as Cloudflare has setup a website to test TLS 1.3 in your browser (Adobe Flash is used for maximum compatibility). In my case only IPv4 worked, since my ISP does not support IPv6, but I got no problem with TLS 1.3.
If the TLS 1.3 test fails, you can contact Cloudflare by email with your test identifier, middlebox information if you’re in a corporate environment, or ISP name if you are on a residential network.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





” with 1.0 and 1.1 still supported by many servers for backward compatibility with older browsers, including the one running this blog. ”
-> I think your blog is not using 1.0 anymore ?
@JotaMG
https://www.ssllabs.com/ssltest/analyze.html?d=www.cnx-software.com
My former comment disappeared, so here a next try without URL: the tool ‘testssl’ is very handy for testing TLS of websites and other services.
Ah, that comment appeared, so here are the results for cnx-software.com:
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered
TLS 1.1 offered
TLS 1.2 offered (OK)
TLS 1.3 offered (OK): draft 18
SPDY/NPN h2, spdy/3.1, http/1.1 (advertised)
HTTP2/ALPN h2, spdy/3.1, http/1.1 (offered)
OK, and here is the URL: https://github.com/drwetter/testssl.sh
Sidenote: it’s 2017, almost 2018, and Cloudflare deploys a website that needs … Flash? OK …
@Sander
They explained that Flash was the only way to access raw sockets from the web browser for most platforms.