WiFi is omnipresent on most connected hardware, and when it works it’s great, but when there are issues oftentimes they can not be solved because the firmware is a closed-source binary. I understand companies do that either to protect their IP and/or make sure end-users do not break FCC compliance.
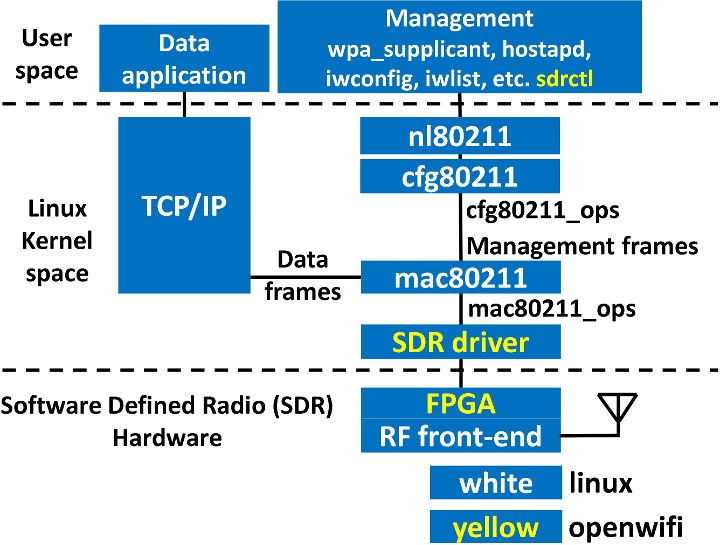
OpenWiFi project aims to deliver a completely open-source SDR (Software Defined Radio) WiFi implementation compatible with Linux and running on FPGA hardware.
OpenWiFi currently supported features:
- 802.11a/g; 802.11n MCS 0~7; 20MHz
- Mode tested: Ad-hoc; Station; AP
- DCF (CSMA/CA) low MAC layer in FPGA
- Configurable channel access priority parameters:
- duration of RTS/CTS, CTS-to-self
- SIFS/DIFS/xIFS/slot-time/CW/etc
- Time slicing based on MAC address
- Easy to change bandwidth and frequency:
- 2MHz for 802.11ah in sub-GHz
- 10MHz for 802.11p/vehicle in 5.9GHz
The developers tested OpenWiFi on Xilinx ZC706 FPGA evaluation kit coupled Analog Devices fmcomms2/fmcomms4 RF board to form an access point, and connected it to a client with TL-WDN4200 N900 dual-band WiFi USB Adapter. iperf results:
- AP to client performance: 30.6Mbps (TCP), 38.8Mbps (UDP)
- Client to AP performance: 17.0Mbps (TCP), 21.5Mbps (UDP)
Here’s a demo of a smartphone connecting to the access point running OpenWifi.
Future and on-going work include 802.11ax WiFi 6 implementation, and support for more hardware platforms including ADRV9361-Z7035/ADRV9364-Z7020 + Analog Devices ADRV1CRR-BOB, as well as Xilinx ZCU102 + Analogic Devices fmcomms2/fmcomms4/ADRV9371.
You’ll find resources such as driver and FPGA code on Github. Note the source is released under two dual licenses: AGPLv3 for open source code and a non-opensource license is also proposed for projects that require it. If you don’t own the fairly expensive hardware to run the demo, you could also check their test bed w-iLab.t tutorial. We were also informed the developers plan to present their project in the “Free Software Radio” devroom at FOSDEM 2020.
Thanks to Zoobab for the tip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





“We were also informed the developers plan to present their project in the “Free Software Radio” devroom at FOSDEM 2020.”
They will have a permanent booth as well.
That’s really cool stuff!
Are there any inexpensive hardware that one can test this on?
Most non-commencial projects fail without cheap hardware.
From the author, it needs around 27K LUTs. But there is room for optimisation.
Cheap FPGAs are here, but far from the 27K:
https://www.cnx-software.com/2019/10/15/5-tang-nano-fpga-board-gowin-gw1n-littlebee-fpga/
You could probably cut through the features (disable encryption support and al) and see how far you could strip down the code to lower down the LUT requirements.
The boards currently used by the project costs over $2,000.
I can see Zynq-7010 has 28K LUT so it might be tight, but there are ~$100+ boards with it:
https://www.cnx-software.com/2015/03/03/myir-tech-announces-low-cost-rico-and-z-turn-boards-powered-by-ti-am437x-and-xilinx-zynq-7010-socs/#z-turn-board
https://www.cnx-software.com/2013/08/07/199-microzed-is-a-low-cost-version-of-zedboard-armfpga-linux-development-board/
You’d still need to add the RF board though.
I have a Parallela board laying around, I think it has a Zynq 7010.
>You could probably cut through the features (disable encryption support and al) From what I can see from a quick skim of the driver/verilog sources they are only really doing the bare minimum for a softmac interface and encryption etc is going to be done by mac80211 on the host side. I could be wrong but I could neither find the hardware blocks for it or the flags needed for mac80211 for any hardware offload features. And to be honest that’s all they really need to do; This is never going to rival cheap broadcom based module for generic wifi… Read more »
You are right. Currently the encryption/authentication rely on Linux mac80211 and libraries above. The only offloading thing is frame filtering on FPGA. It is true that it is beaten by commercial chip no doubt. As the first step, the competitor/target is not commercial Wi-Fi chip. The counter parts are “WARP 802.11 design” and “NI Labview 802.11 framwork”. But still, really thank you for the comments! We will definitely think about it.
Thanks for the comments. Your are right. Currently all encryption/authentication are rely on Linux mac80211 and above. The only offloading is frame filtering functionality on FPGA.
Sure the openwifi can not beat commercial chip. We 120% aware and agree that.
The first competitor/target is not commercial Wi-Fi chip. The counter part is the Wi-Fi SDR reference design, like “WARP 802.11 design” and “NI labview 802.11 framwork”.
next step is this board: ADRV9361-Z7035, 1100 dollar
https://www.analog.com/en/design-center/evaluation-hardware-and-software/evaluation-boards-kits/adrv9361-z7035.html
Then this board: ADRV9364-Z7020, 550 dollar
https://www.analog.com/en/design-center/evaluation-hardware-and-software/evaluation-boards-kits/adrv9364-z7020.html
” If you don’t know the fairly expensive hardware to run the demo, ”
Guess you mean “own”, not “know”