Security is becoming more and more important with critical data exposes to the Internet. Traditionally some PCs, laptops, motherboards, or single board computers would be equipped with a TPM (Trusted Platform Module) designed to secure hardware through integrated cryptographic keys. More recently, we’ve started to read more and more about secure elements providing hardware-based security for lower-end platforms.
Those are external chips, but companies have also started to providing hardware-security within the processor with solutions such as Arm Trustzone or Intel SGX (Software Guard Extensions). But more recently, Google and Microsoft have made announcements about hardware-security IP with respectively OpenTitan open source project and Microsoft Pluton security chip both meant to be embedded into processors.
OpenTitan
 OpenTitan is described as being “the first open-source project building a transparent, high-quality reference design and integration guidelines for silicon root of trust (RoT) chips”. It is backed by Google, Seagate, Nuvoton, Western Digital, lowRISC, and other companies, projects, and universities.
OpenTitan is described as being “the first open-source project building a transparent, high-quality reference design and integration guidelines for silicon root of trust (RoT) chips”. It is backed by Google, Seagate, Nuvoton, Western Digital, lowRISC, and other companies, projects, and universities.
It was announced last year, but Google recently published an update detailing some of the progress made by the project:
- More than doubled the number of commits at launch (November 2019): from 2,500 to over 6,100 (across OpenTitan and the Ibex RISC-V core sub-project).
- Grew to over 141K lines of code (LOC) of System Verilog digital design and verification.
- Added 13 new IP blocks to grow to a total of 29 distinct hardware units.
- Implemented 14 Device Interface Functions (DIFs) for a total 15 KLOC of C11 source code and 8 KLOC of test software.
- Increased our design verification suite to over 66,000 lines of test code for all IP blocks.
- Expanded documentation to over 35,000 lines of Markdown.
- Accepted contributions from 52 new unique contributors, bringing our total to 100.
- Increased community presence as shown by an aggregate of over 1,200 Github stars between OpenTitan and Ibex.
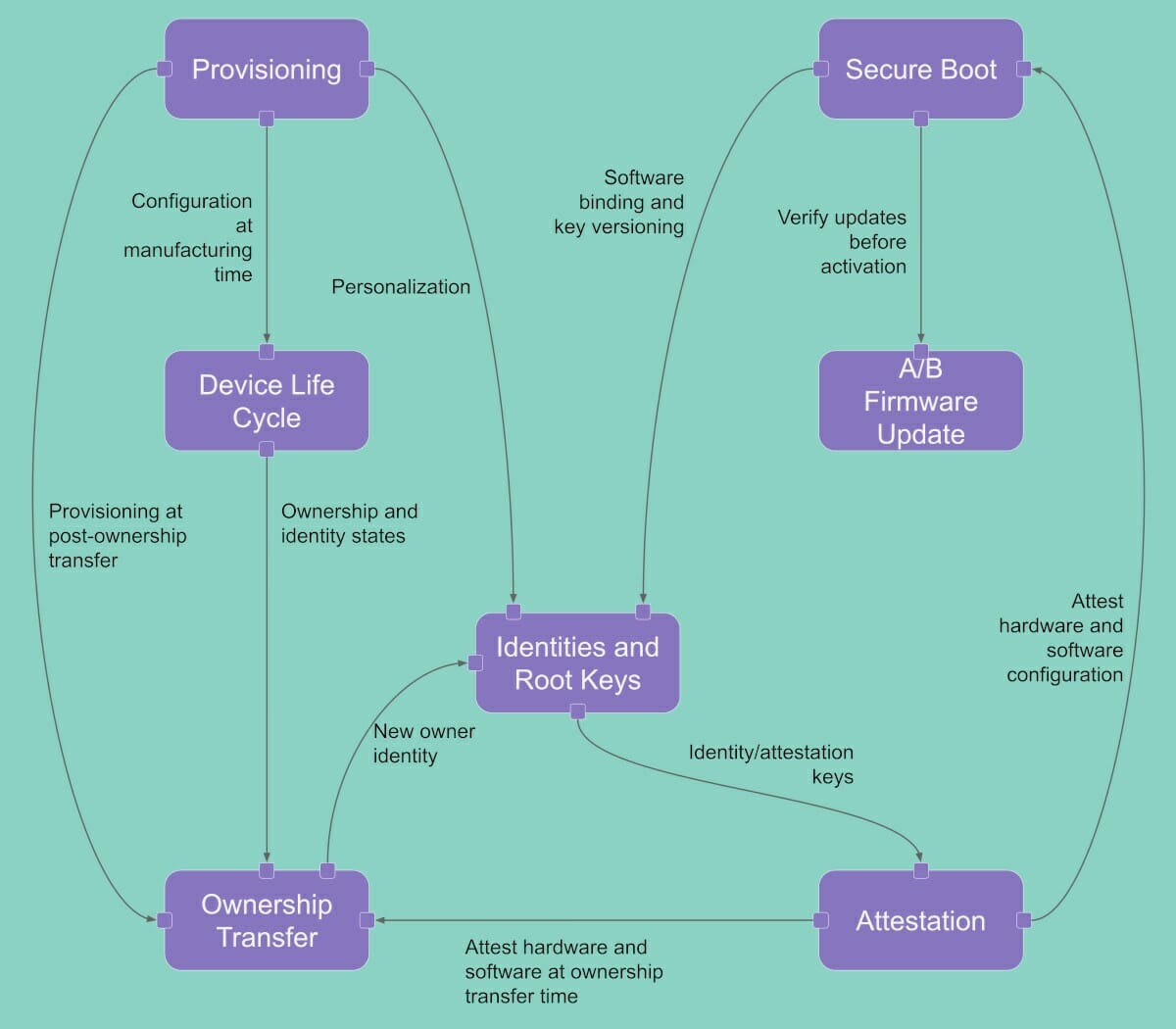
The company also said OpenTitan is the first project to publish an open Security Model for a silicon root of trust and covers provisioning, secure boot, device identity, and attestation, and our ownership transfer mechanism, among other topics.
Since OpenTitan is open-source any chip designers could integrate it into their processor(s), but there’s no ETA for when this may happen, as the project still seems to be a work in progress. You’ll find all details on the main website.
Microsoft Pluton
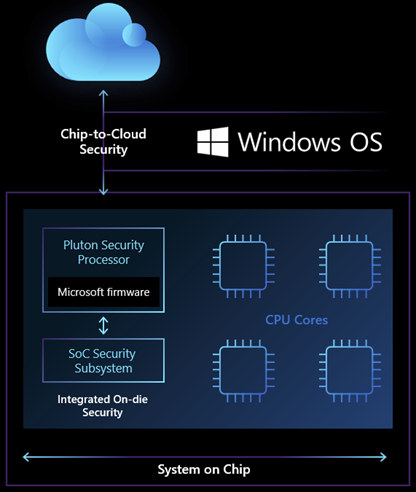
On the other side, we have Microsoft Pluton that was first introduced in 2018 inside MediaTek M3620 Cortex-A7/Cortex-M4 processor with support for Microsoft Azure Sphere OS. The main news for 2020 is that Microsoft announced Pluton will now aim to replace the external TPM chip with an embedded hardware-security solution built into Intel, AMD, and Qualcomm processors found in Windows PCs and laptops.
Based on the diagram above, it appears Pluton may address a different layer of the security stack compared to OpenTitan, as it acts between the SoC security subsystem and the cloud, and is designed to provide more secure cloud connectivity. External chips may be prone to physical attacks, with a bad actor capable of capturing data between the processor and the TPM using a logic analyzer, and then work on the capture data, but this would be much more challenging or even impossible to do the same with Pluton security processor as it’s part of the main SoC.
Other advantages touted by Microsoft include support for the Open Compute Project’s Project Cerberus providing a secure identity for the CPU, and the ability to keeping the system firmware up to date more easily as Pluton firmware updates will be delivered through the Windows Update process.
Just like with OpenTitan, there were no specific processor announced with Pluton, nor specific availability announcement, but I’d assume some of the processors from Intel, AMD, and Qualcomm announced or launched in 2021 will come with Pluton security chip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.




When the article states:
“External chips may be prone to physical attacks, with a bad actor capable of capturing data between the processor and the TPM using a logic analyzer, and then work on the capture data, but this would be much more challenging or even impossible to do the same with Pluton security processor as it’s part of the main SoC.”
I am reminded of this:
https://xkcd.com/538/
I think a lot of people in the Linux community are going to ditch AMD and Intel forever if they put this in every chip. We don’t trust Microsoft, we don’t want Pluton. AMD Zen 4? More like Zen Forget-about-it.
>I think a lot of people in the Linux community
I think you shouldn’t really assume you know what everyone in “the community” wants or believes.
>are going to ditch AMD and Intel forever if they put this in every chip.
Big cloud vendors that make up a massive chunk of the linux world want this stuff..
“IoT” style devices that run linux and are sold in their thousands to millions also want this stuff.
>We don’t trust Microsoft,
Yet Sasha Levin, someone that works at Microsoft, is one of the LTS kernel maintainers..
Yes those 5 nerds will definitely hit sales of the big cpu sellers…
Exactly as noone buys iphones and macs and Samsung mobiles…
These things have absolutely nothing to do with security, “security” is just a pretext to sell it. This only about easier vendor lock-in, as usual. This cannot help at all with security because the vast majority of *real* security issues come via the browser, HTML emails and encrypted ZIPs. That’s how machines are intruded, how data are stolen, and how PCs are encrypted by ransomware. As one can see, these chips are totally unrelated to these problems affecting the real world.
Well let’s assume such a chip comes from an universally trusted entity, and every developer can get certified then every single snippet of JS could be signed and verified pre execution…
That’s exactly the dream of crypto people who have zero knowledge about real security. They imagine a world of maths where everything works as designed with zero bug. And the whole attack surface is entirely eliminated thanks to complex crypto algorithms… Until an out-of bounds access, low-power condition, intercepted suspend-resume cycle or whatever that doesn’t exist in the model happens, and the whole protection flies into pieces. Have you seen a worse trust model than SSL for example ? Everyone trusts it (no other choice) yet it’s never the crypto that’s attacked, simply the weak extremities (when it’s not just the user who’s fooled by typosquatting or unicode homoglyphs).
Well it might help stopping the biggest morons from shooting their own foot.
And for the rest of your arguments I guess my universally trusted entity should already be enough of a hint…
I’m not totally sure on that. We’ll see when things actually ship and who gets to set the keys. If the user can set their own keys then this is interesting.. but I’m guessing it’ll be the same story were some vendor has the keys for your own good.
That will be interesting foryou, me and a couple others…
Secure boot is the first thing I’m usually disabling, but tbh how can you expect normal admins, let alone users can be tasked with key management?
That’s why the crypto of WA and Signal just works, it’s out of every ones way. But if a device is locked by its vendor or MS or… I won’t want to own it.
My phone for example is currently locked but I know I could back all up and then unlock it, so for now and for a phone that’s ok.
For my parents i.e. I feel better when it has a certain out of the box “security” but for me that’s different and I learnt that I’m not the targeted audience of most things…
It’s for the money. Windows will be like Office 365 is already – pay every month and use it. You didn’t pay? Well, sorry, but your security chip wont let you run it anymore. Maybe it will let you run some “Pay with X, Y or Z” app. “Your” data in the “secure” Cloud of course, because why anyone needs a privacy? Only terrorist and other bad guys (and girls?) need privacy. Brand new world ahead.
I will NEVER buy a CPU or Phone with Pluton in it. Corporate greed – Full ID & Device Control – No!