There are many examples of Internet of Things projects, but more often than not the implementation is not secure, either because the device is exposed to the Internet with minimum or no security (worst case), or a gateway (hopefully) provides secure connection to the Internet, but the communication between sensor nodes and the gateway in the local network is not secure, due to memory limitation of the nodes, for example it might be challenging to implement security on ESP8266. Mongoose OS is an open source operating system for the Internet of Things developed by Cesanta working on ESP32, ESP8266, STM32, and TI CC3200, and the developers have demonstrated a secure solution with Mongoose OS running on ESP8266 connecting over a TLS connection to AWS IoT (Amazon Web Service IoT) and using TLS credentials stored in Microchip ATECC508A CryptoAuthentication Device.
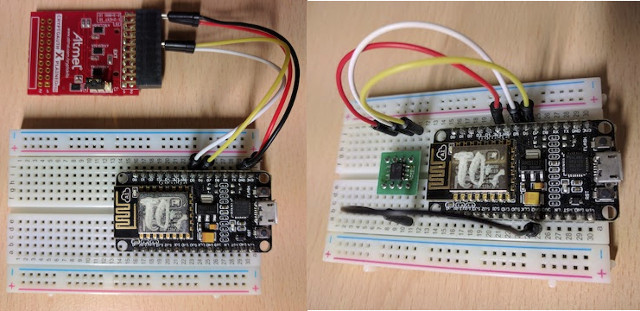
The addition of ATECC508 chip either using “XplainedPro extension board for crypto products” (ATCRYPTOAUTH-XPRO) or ATECC508A chip itself, is to avoid storing private TLS credentials in NodeMCU’s flash memory, as anybody with physical access to the device could steal private keys and get access to the cloud. ATECC508A is connected via the I2C interface of the target board.
So I guess the crypto chip truly makes sense if you have sensor nodes on the field with information important enough that third parties may be interested in getting access to your sensor to try read your private key from ESP8266’s flash. It costs less than $1, so you may consider it anyway, although you can still get a secure TLS connection between NodeMCU and AWS IoT without it, but it adds another level of security.
Once you are done with the hardware connections, you’ll need to install Mongoose OS on the board, and follow the MQTT + AWS IoT tutorial to get started. Nothing complicated need to be done to leverage the crypto chip, as the command mgos aws-iot-setup should automatically detect ATECC508A chip and use it.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.




Well esp8266 should be able to run Curve crypto.
@zoobab
yes, it is capable of doing it, though it’s a bit slow at it (takes a couple seconds). point is, with crypto chip the private key is not accessible to someone with physical access to the device. crypto chip also makes handshake faster, which is a nice bonus (but also doesn’t matter much for AWS IoT connection, as it is done in the background).
Someone with physical access can just take the crypto chip and attack it MITM. ESP weakness is that all code is in an external flash chip.
Not directly related to this project, but still related to security.
According to Wikileaks a bunch a CIA hacking tool (several hundred million lines of code) have been shared among former U.S. government hackers and contractors: https://wikileaks.org/ciav7p1/#PRESS
They targets android and iOS phones, smart TVs, routers, cars, and also computers (Windows, OSX, Linux…)
Wikileaks named the release “Vault 7”.
This promises to be a lot of fun…
@Pooma
that’s true, there’s no way to protect code on esp8266 since there’s no secure trust anchor.
still, external chip for credential storage means e.g. you cannot clone the device (not without cloning the chip, anyway).
for full protection you need to go to esp32, which has flash encryption and secure boot.
also supported by mongoose os.
@Pooma
@Pooma
Agree with you on the potential for a MITM attack over I2C. Zymbit security module for RPI isolates the ATECC508A from the user app with a secure MCU. ATECC508A to MCU is ofcouse encrypted. More details here. https://www.zymbit.com/zymkey/#Cryptosilicon
Mongoose is quite interesting – not so newcommer friendly as arduino for esp, but quite well implemented – I meant that not-so-huge codebase is the only negative aspect of the mongoose.
In recent weeks they also implemented some kind of arudino compatibility so one could benefit from large code base for arduino and still get the high end features of the mongoose.
I think that “mgos” is old name – now the tool is renamed, “mos” if I remember right. This makes some articles obsolete (not working directly with copy/paste).
@gicho we’re doing our best to keep docs / articles up to date, so that should not be a concern.
You mentioned Arduino is more friendly to the newcomer than Mongoose OS, could you elaborate why, please?
@cnxsoft
Thanks for mentioning security relevant issues one more time. My favourite is turning so called ‘smart’ TVs into simple bugs that spy on you. But TVs with a single mic are boring, those Alexa or this ‘Hey Google’ thingies with microphone arrays are way more interesting since they get you even when you just whisper somewhere in your own house 🙂
@cpq
Yes, I think I just hit a time slice when you changed the name of the tool and there were some issues with code build. Also I acknowledge that you fixed it in several hours after github issue report.
About newcomers – my point was about DIY users, not professional programmers. With arduino one could easily build his first project by “copy-paste” with some help from google search. This attracts people with less expirience – at least doesn’t scare them away. Some days later working on the project they will find out the real need of provisioning, OTA update, configuration – both “manufacturer” and “end user” and so on. But most of DIY projects end up with hardcoded configuration (wifi credentials, mqtt broker account, even sensor poll time) and are “deployed” by rebuilding the sketch with the new ones.
For example, the Espressif SDK for 8266 was quite nice – callbacks/events instead of superloop, much better than setup()/loop(). But the real boom in user base came only when the ESP8266 Arduino IDE was ready.
The ESP8266 was not useful for anything “commercial” because of total lack of code protection, so no one would put money in development products that could be clones with $5 SPI programmer.
> Download mos.exe; double-click mos.exe
This is a CTF, first idi-ocy-proofness stage, right? Like, if someone talks you about secure chip and other b/s and tells to download and run .exe, and you laugh in their face, then you can proceed to the next level?
https://github.com/cesanta/mongoose-os/tree/master/mos
I believe these are the sources for the tool. Pre-built exe allows newcomers to jump start.
@gicho
Thank you, very well said.
Yes, if you want to build it yourself you can just use Mongoose OS sources from GitHub. This is an open source project.
Downloads are for the MOS tool, which significantly simplifies firmware built the process through either terminal/command prompt or UI.
@cnxsoft
Glad to see the CIA is also working on Embedded Software too…. They’ve hacked iPhones and Mac computers’ firmware so that it does not override their hack even if you reinstall the OS. -> https://twitter.com/wikileaks/status/844897244155392002/photo/1
@cnxsoft
Just do a web search for ‘De_Mysteriis_Dom_Jobsivs_Black_Hat_Paper.pdf’ (2012) where everything is explained in detail. (U)EFI rootkits are nothing new unfortunately and I would believe some of these vulnerabilities can be considered design goals of the technology.