FUZE Card is a Bluetooth enabled card with ePaper display that can store up to 30 real credit card. You’d program credit cards into it via Bluetooth Smart (BLE) using a smart phone app, and use it like a normal credit card while paying, after selecting the card you want to use. It’s more convenient than carrying many cards, and more secure since part of the number are hidden (shown as stars ****), so whoever get your card can’t easily make a copy of the information.
A problem however is that according to ICE9 Consulting, there’s a security vulnerability that allows credit card numbers to be stolen via Bluetooth: CVE-2018-9119.
The full details can be found on ICE9 blog post. They started to make a X-Ray to find out about the main components see (photo below), and the reverse-engineered the Bluetooth protocol using an Android smartphone, and software tools such as Burp Suite (optional),Wireshark + crusty Perl scripts, and gatttool / BlueZ.
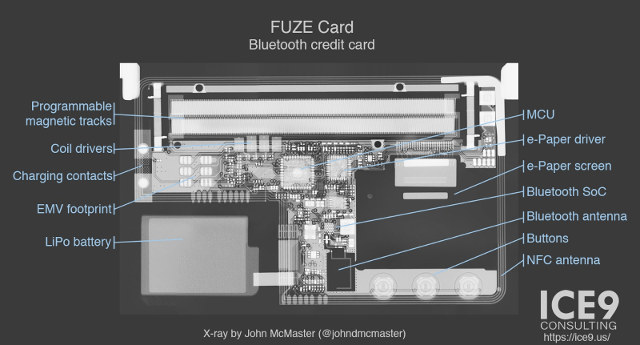
Read their blog post for the full details about the Bluetooth protocol used and vulnerability, but the takeaway is that an attacher with physical access to a FUZE card can:
- Bypass the lock screen.
- Read credit card numbers with expiration date and CVV.
- Tamper with data on the card.
The card is described and the vulnerability showcased in the video below.
ICE9 Consulting has tried to contact the company making the card (BrilliantTS), but did not get feedback until the flaw was made public, and now the company plans a fix on April 19 with both new firmware and mobile apps.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress






And this is why i dont trust any of these “smart” IoT devices
What exactly makes this IoT? As far as I can tell, it doesn’t connect to the internet.
The problem is that vendors are making stupider and less secure devices everyday just to satisfy a majority of stupid and lazy consumers who don’t care a single second about their security provided they can save 3 seconds on average in payment time. The day banks and insurances will refuse to refund losses in case of manipulation error, communication hijacking or device intrusion over the air, things may have a chance to change. Until then it’s out of luck sadly, and we have to suffer from these new devices replacing the previous ones.
The way to secure devices is money. Make the Bank, card company and shop, liable for 5 times what is stolen. Theft will be eradicated over night. At present they just put the cost on, accounts administration charges.
Will not work : if such a rule is put in place, the next year a law will appear increasing the charges against attackers. Right now if an ATM has a vulnerability and you exploit it to retrieve more money than you paid for, guess whom is sued ? Not the bank, not the ATM vendor, you. Incompetence is protected by law in many countries.
Check this notice. https://fuzecard.com/security_notice.html