Last year’s Eclipse IoT Survey Report shows evidence that security is one of the major reasons for the development of IoT devices. As the number of IoT and embedded devices increases, we see a constant increase in the need for security issues in IoT and embedded devices. There have been increasing security expectations from device end customers and buyers to gain security insights and risks related to their connected devices.
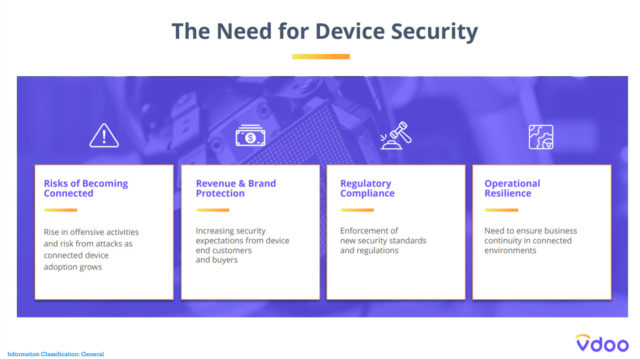
Security requires time and effort, so when a new product is launched in the market for business reasons, security compromises may have to be made. Also, organizations don’t have the capabilities and tools to get in-depth information about connecting device security. This is mainly due to the complex chain of third-party products.
Methods for Detecting Security Issues
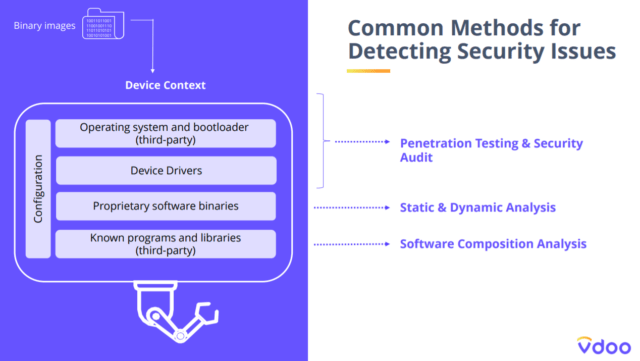
Solutions
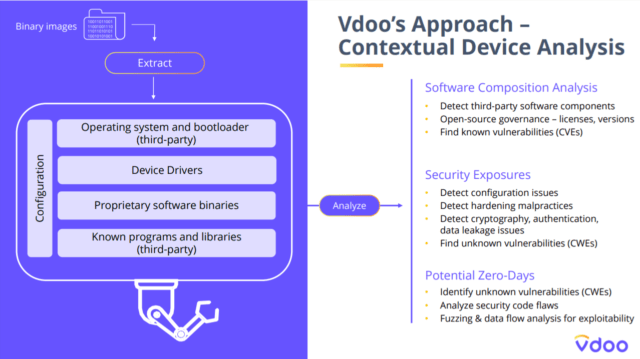
The above methods are combined into this platform by VDOO. It starts with the device binary image as the device software in binary format and is loaded into the device. In many cases this is the one-way attackers have access to the system. Then use a combination of analysis techniques and machine learning to detect known vulnerabilities CVEs, detect third party software components. Finally, identify potential zero days by finding problematic parts of the code and analyzing them for exploitability in the device context by leveraging data flow analysis, symbolic execution, and fuzzing.
Benefits of this solution
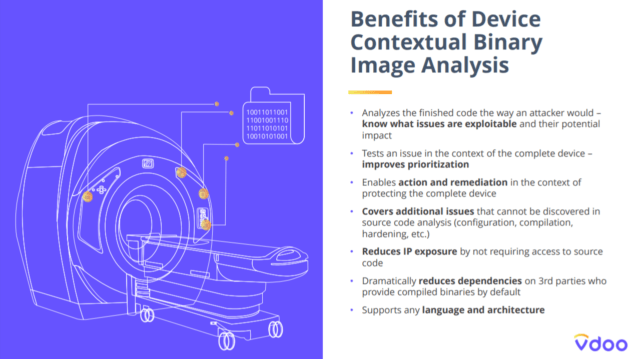
It analyzes the finished code the way an attacker would, this will help to know what issues are exploitable and their potential impact on the system. It also covers additional issues that cannot be discovered in source code analysis. This will dramatically reduce the dependencies on third-parties who provide compiled binaries and support for any language and architecture.
Source: All the images were taken from the talk by Yaniz Nissenboim at the IoT Security Summit 2020.

Abhishek Jadhav is an engineering student, RISC-V Ambassador, freelance tech writer, and leader of the Open Hardware Developer Community.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.



