Data is can be extremely valuable, so Alt Shift designed the BusKill USB kill cord that will automatically execute a user-configurable trigger when your machine is physically separated from you. It can be especially useful to journalists and activists that may get their devices seized by the government, crypto traders, military personnel, or travelers with sensitive data.
BusKill is basically just a USB cable attached to the computer via a magnetic breakaway and to the user, for instance to a belt loop, and that will trigger a configurable Python script if the cable is detached while BusKill software is armed.
BusKill is made up of four hardware components with a custom magnetic breakaway, a standard USB extension cable, and a USB thumb drive attached to a carabiner via a keyring. I could not find a clear explanation for the USB thumb drive in this system, but I can only assume it’s for USB removal/insertion. BusKill is fully open-source, and you’ll find the python scripts and GUI, as well as OpenSCAD files for the magnetic breakaway on Github. A separate website also provides documentation with more details, such as the operating systems supported: Windows 10, Mac OS 10.05, as well as Ubuntu 20.04/18.04.
BusKill can be armed/disarmed from the command or the GUI program, and there are different levels of protection for your system. By default, the program will not destroy any data, and simply turn off your computer if the USB cable to disconnected while BusKill is armed. But the solution offers more flexibility, especially for advanced Linux users that can manually add auxiliary triggers, such as a self-destruct trigger that wipes the LUKS header, making the entire disk permanently inaccessible.
This brings the topic of accidental unplugging, where you could potentially get your data wiped out while forgetting your USB kill cord is attached to your computer. Alt Shift addresses that issue in a FAQ:
BusKill’s breakaway connector uses strong magnets that decreases the risk of false-positives.
That said, it is designed to breakaway, so if you accidentally trigger BusKill (by, say, standing up to get a cup of coffee without disarming BusKill), then the worst that can happen (if you’re using the BusKill app without manually adding auxilary triggers) is that your computer will shutdown.
Here’s some tips to avoid false-positives:
- When using BusKill, work on a sturdy table with a comfortable chair.
- Avoid moving your laptop after arming BusKill in the app.
- The first few days, limit yourself to just the lock screen trigger to avoid loosing your work as you get used to disarming BusKill before taking toilet breaks.
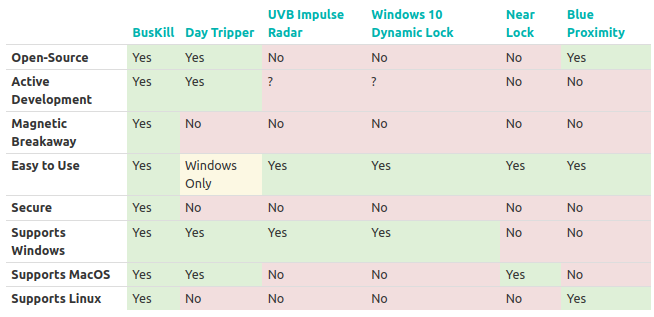
Similar systems have been designed in the past with most relying on Bluetooth or 2.4 GHz ISM with solutions such as DayTripper, but it may not be as secure due to potential attacks like radio jamming and replay attacks.
The complete BusKill Kit has just launched on Crowd Supply for $89 or the company’s own store if you want to pay with cryptocurrencies. Shipping is free worldwide, and orders are expected to ship by June 2022.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress






I do not see why dedicated hardware is needed for this. You just need to detect that a USB device was unplugged, and possibly apply a probation period before deciding to lock/turn off/wipe the PC. You could decide to do that even with your own USB flash disk and register your serial numbers, and if none of them are reinserted within 10 seconds you lock it down. All this looks like a lot of complications to me for little to no extra benefit. Or maybe I’m just confused and it does extra stuff that I’m not seeing ?
It’s probably about speed. If a user has to remove the USB dongle manually it may take a few seconds, something he/she may not have time to do if the laptop is snatched or an FBI SWAT team enters the room.
And shoots you for wearing a suspected bomb ? 🤐
You still can decide to use a usb extension cable (with a usb flash drive at the other end (and e.g. tie that to your belt). If someone snatches your computer the connection will quite likely break;
Of course using magnetics has some benefits
Yes that was my point, just connect that device after an extension cable attached to the table or anything else and that’s done. Furthermore, nowadays with USB power supplies you could even have a chip inside the PSU so that the PC detects unplugging.
Yep, no need to pay $89 – anything that looks like usb and simple udev rule:
That’s exactly what I meant (except I still can’t write udev rules without googling first :-)).
I was thinking that exactly, just tie the script to a specific ID xxxx:yyyy, and make the script run shutdown so that on boot a LUKS passport has to be entered, or even wipe the LUKS keys.
The only main difference seems to be that it has a special magnetic attachment which is probably calibrated to a comfortable level of pulling force.
Hmmm… I get that this has potential uses, but… I guess if you have whole-disk encryption and hardware security measures, then the shutdown might be effective, but it is generally accepted that once ‘they’ have hardware access it’s game over. So it seems to me that the only *real* way to be completely secure would be the self-destruct – but then again, I feel like this would inevitably end in the user accidentally wiping their drive :\ So here’s my thinking: if you want to have the self-destruct capability, boot off a relatively disposable USB drive, either internally or externally.… Read more »
if you wipe any LUKS keys, and force a rapid shutdown, then the attacker can’t just turn the machine on, and you as the owner would have to recover the LUKS keys from a backup which you can arrange to be at a secure location.
The USB thumbdrive on the carabiner allows you to keep the documents on your person even if the device you used to work with those documents is grabbed from you. It won’t stop the documents being taken if you are physically searched, but it does provide some window of opportunity for retention if only the device is grabbed and the thumbdrive is left attached to you. That’s good for theft protection, but not much more. As for LUKS header – once you have mounted the drive you can wipe the LUKS header. No need to wipe it in real time.… Read more »
As a former police officer from Eastern Europe, I can tell you, that in most countries, where your device may be snatched forcibly from you, you will be giving all your LUKS keys, headers or whatever to those guys just after couple rounds of waterboarding or any other kind of torture.