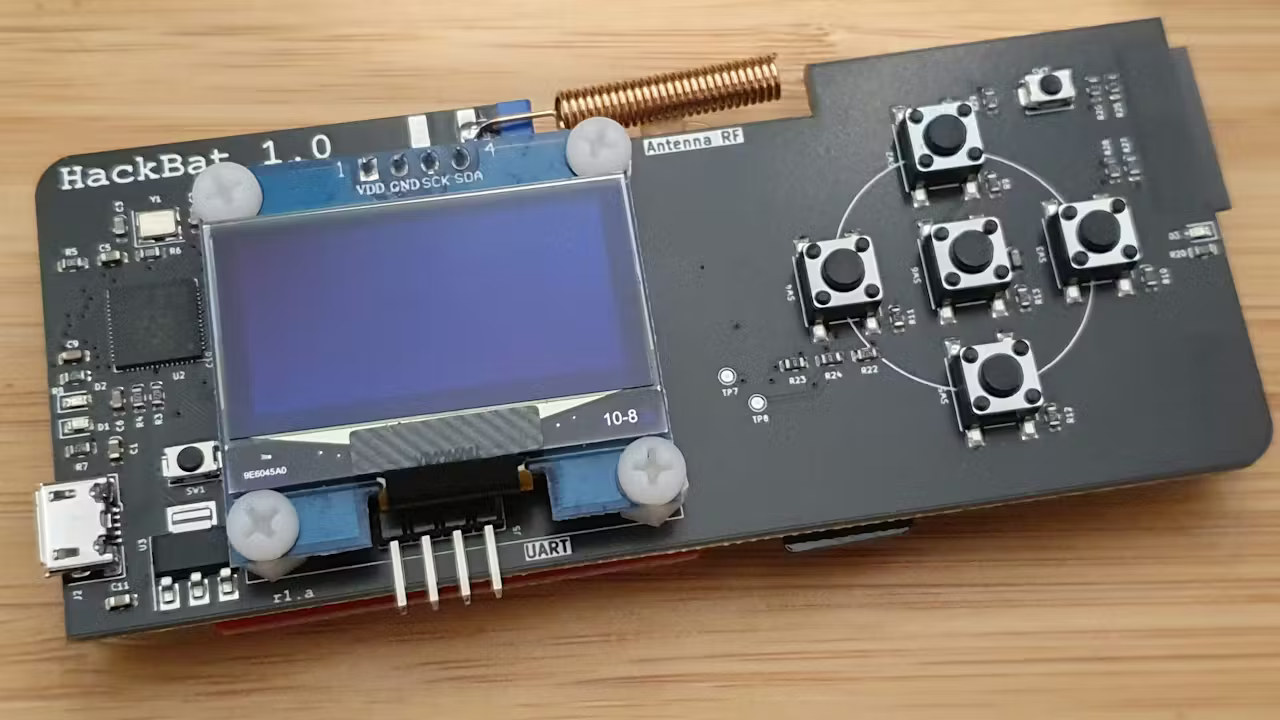
HackBat is an open-source hardware pen-testing device designed for hackers and makers and equipped with a Raspberry Pi RP2040 microcontroller, an ESP8266 WiFi module, a sub-GHz RF transceiver, NFC, an OLED display, and more… It’s basically a DIY alternative to the popular Flipper Zero wireless hacking tool, that you can produce and assemble yourself. The Flipper Zero was the victim of its own success with the Canadian government (wrongly) claiming it could easily be used for car theft and planning to ban it (status still unclear right now), so Flipper Zero alternatives such as the M1 multitool device got some traction as backup solutions with some extra features. But any closed-source device could eventually be banned, something that’s close to impossible for an open-source hardware device like the HackBat although policymakers could still decide to impose heavy fines if they wanted to make this type of device illegal… HackBat key […]
The M1 device is a Flipper Zero alternative with a faster STM32H5 microcontroller and Wi-Fi connectivity (Crowdfunding)
The M1 is a multitool device that bundles several hacking and penetration tools in a package that looks like a retro-gaming console and could be viewed as a Flipper Zero alternative with a more powerful STMicro STM32H5 Cortex-M33 high-performance MCU featuring Arm TrustZone hardware-based security for additional protection for sensitive data. The M1 multitool device features transceivers for infrared, sub-1 GHz, Bluetooth, NFC, RFID, and Wi-Fi. This means that the M1 can replace most of your remotes as well as your RFID and NFC-based items (membership cards, access fobs, business cards, credit cards, etc.) It also has twelve 3.3V (5V tolerant) GPIO pins that can be used to add extra functionality to the device. M1 specifications: MCU – STM32H5-series microcontroller, with a 32-bit ARM Cortex-M33 core, 1MB RAM Storage – MicroSD card slot Display – 1.54-inch display, 128 x 64 resolution Connectivity Bluetooth 4.2 BR/EDR BLE Sensitivity -96dBm Infrared – […]
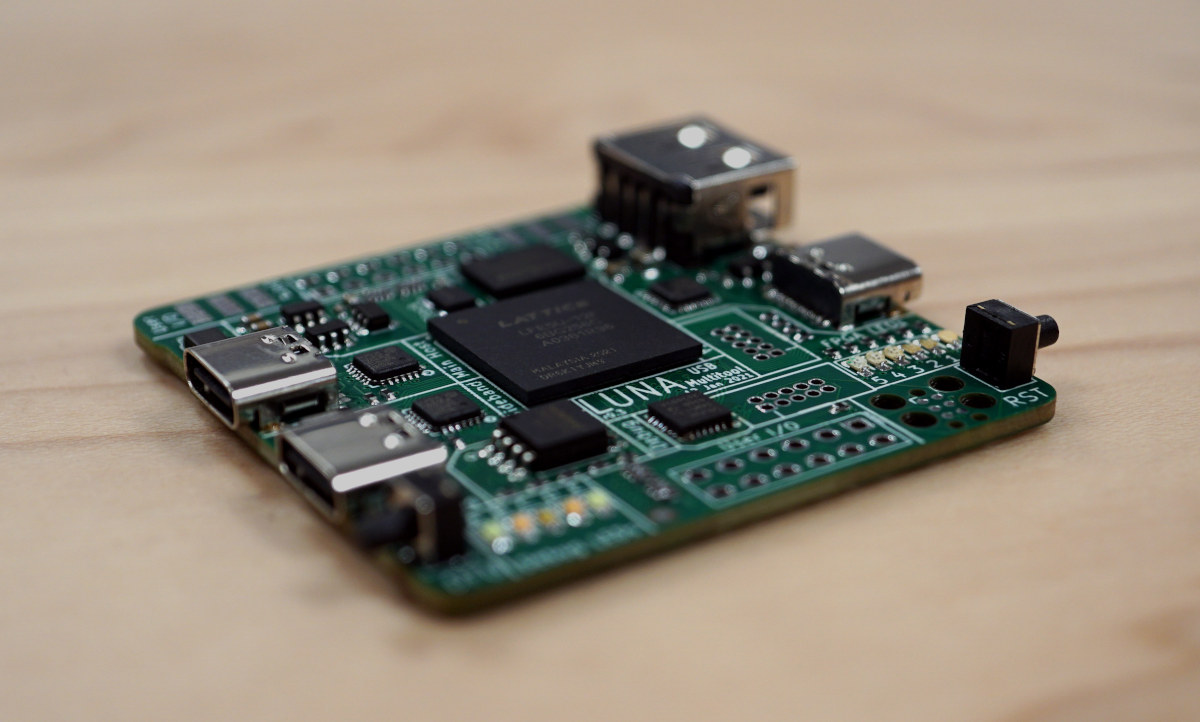
Cynthion board enables USB Hacking through Lattice ECP5 FPGA (Crowdfunding)
Update 16/02/2023: The LUNA board has been renamed to Cynthion, but the gateware framework continues to be called LUNA. Several USB hacking/debugging boards were launched in 2020 either based on microcontrollers or FPGA with the likes of Tigard (FTDI FT2232HQ), Ollie (STM32F042), Glasgow Interface explorer (Lattice Semiconductor iCE40), or Protocol Droid (STM32). All those were launched on Crowd Supply, and there’s now another one with LUNA “multi-tool for building, analyzing, and hacking USB devices” based on a Lattice Semiconductor LFE5U-12F ECP5 FPGA that raised over $100,000 in a few days. Cynthion hardware specifications: FPGA- Lattice Semiconductor LFE5U-12F ECP5 FPGA with 12K LUTs System Memory – 64 Mbit (8 MiB) RAM for buffering USB traffic or for user applications Storage – 32 Mbit (4 MiB) SPI flash for PC-less FPGA configuration USB – 3x High-Speed USB interfaces, each connected to a USB3343 PHY capable of operating at up to 480 Mbps. […]
Security Tip – How to detect Juice Jacking on Android smartphones
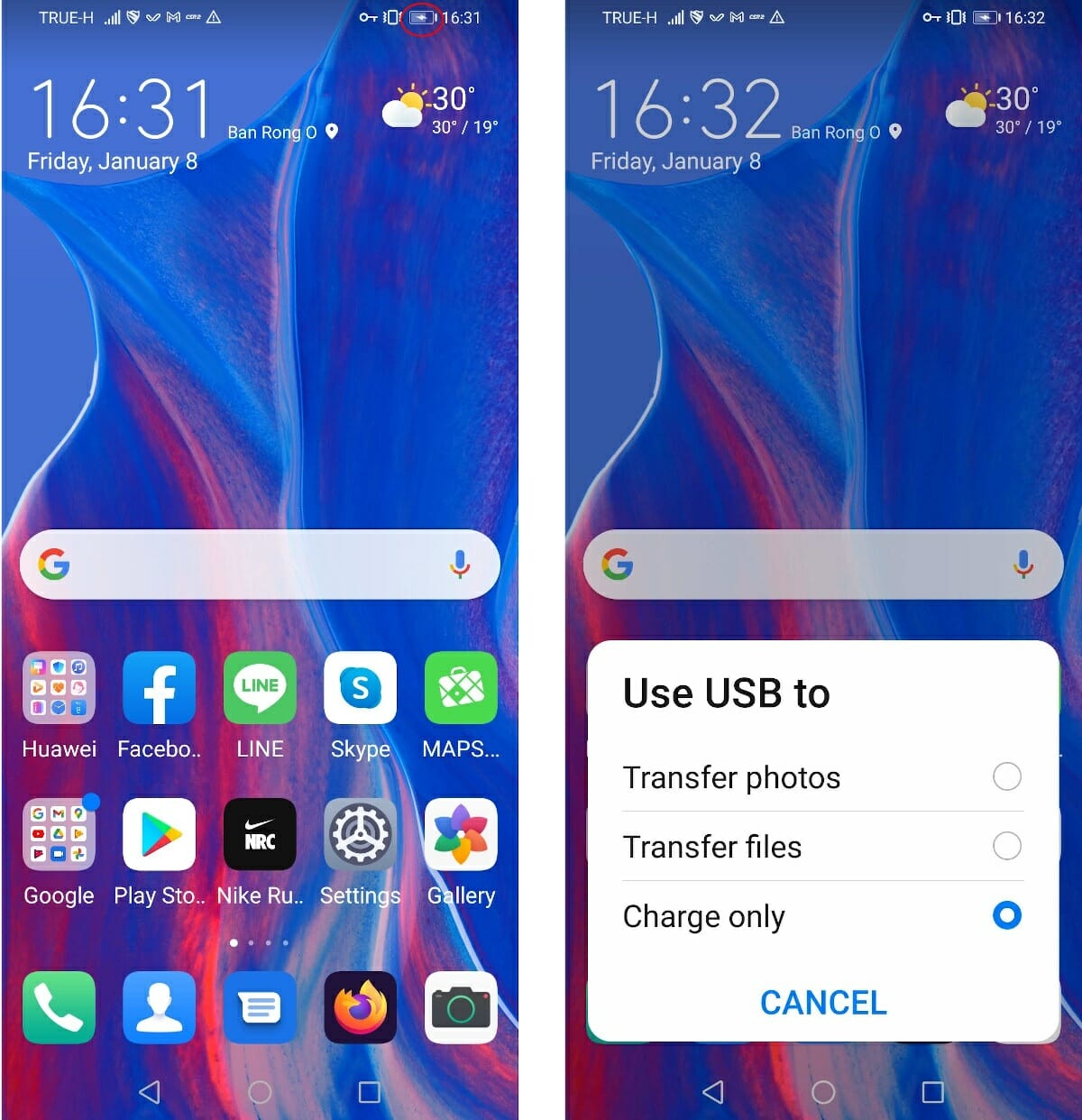
A few years ago I wrote about the danger of “juice jacking” highlighting the security risks posed by USB charging in public places, where a bad actor could attempt to hack your phone or laptop to steal your precious data or install malware/ransomware. In most cases, there are no risks at home, but it’s when you charge your device in a public place notably an airport or train station that you could be at risk of hacking. If you’re using an Android phone, there’s an easy way to detect Juice Jacking, and whether something fishy is going on as shown in the screenshots below. On the left screenshot, I connect my phone to a USB charger, all that changed was the battery icon changed to show it’s charging. But on the right screenshot, I connected my smartphone to my laptop, and since it’s trying to access data, I’m offered three […]