We’ve just seen pfSense is now available for Arm via firewall appliances such as Netgate SG-3100, but AFAIK there’s no pfSense community Arm firmware images yet. Several Arm SoCs & boards are now supported by FreeBSD, so in theory pfSense could be ported to those, but the page on FreeBSD does not seem to have been updated for a while.
If you want a firewall distributions with an easy-to-user web interface like pfSense, but that also works on cheaper Arm hardware, Linux based ZeroShell distribution could be worth a try, as beside working on Intel & AMD x86 platforms, the developers also provides images for Raspberry Pi 2 & 3 boards, and several Orange Pi boards, namely Orange Pi R1, Orange Pi Zero, Orange Pi PC, and Orange Pi Plus/Plus2. The latter is the only supported Arm board with Gigabit Ethernet.
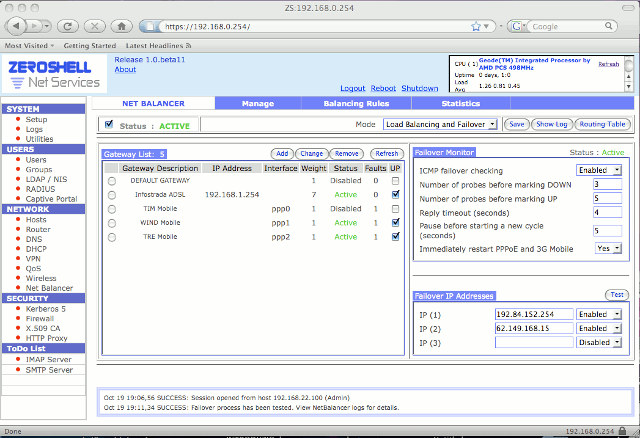
Some of ZeroShell features include:
- Load Balancing and Failover of multiple Internet connections.
- UMTS/HSDPA connections via 3G modems.
- RADIUS server for providing secure authentication and automatic management of the encryption keys to WiFi networks.
- QoS (Quality of Service) management and traffic shaping.
- HTTP Proxy server to block web pages containing virus.
- Wireless Access Point mode with Multiple SSID and VLAN support.
- Host-to-LAN VPN with L2TP/IPsec in which L2TP (Layer 2 Tunneling Protocol) authenticated with Kerberos v5.
- LAN-to-LAN VPN with encapsulation of Ethernet datagrams in SSL/TLS tunnel with support for 802.1Q VLAN.
- Router with static and dynamic routes (RIPv2 with MD5 or plain text authentication and Split Horizon and Poisoned Reverse algorithms).
- 802.1d bridge with Spanning Tree protocol to avoid loops even in the presence of redundant paths.
- 802.1Q Virtual LAN (tagged VLAN).
- Many more…
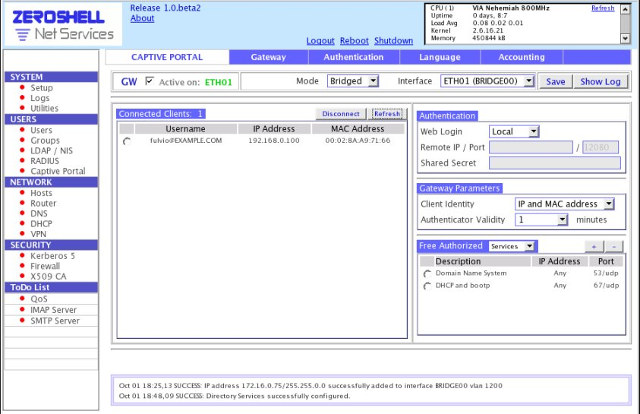
You’ll find the complete list of features on the project page. You’ll find live CD images for x86, and micro SD card image for supported Arm boards on the download page, and support is available via the forums. However, I have not been able to find the source code, nor instructions to build from source.
Via Time4EE

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.




I looked into this a few days ago and kernels used for ARM are a show-stopper: 3.4.113 for H3 or an outdated 4.4 for Raspberries.
We are using zeroshells for office purpose since 4 years on old low power intel (amd64) with two gigabit ethernet.
It runs smoothly, easy to manage, feature full and stable… not a single glitch.
We have done it manually previously, a load-balancing (with tc), vlan, a fail-over (manual scripting), openvpn and iptables… don’t waste your time if you already know all that and install Zeroshell.
If you send a tip to its developer, you get the OTA upgrade.
Thanks
Didn’t know there was a linux alternative to pfsense, nice!, but the gui seems rather outdated, could do with an overhaul.
@jeroen
This is not an alternative to pfSense, at least not with ARM devices. Running something targeted at network security with an Android 3.4 kernel that received latest fixes over half a year ago is impossible.
As soon as the product switches the base to a recent Linux kernel and opens its sources a review process could be started.
@tkaiser
yes, not an alternative with ARM devices.
But the real question is why using small ARM dev board, for most of them with usb ethernet, to build a home or a small enterprise gateway since you can get a rock-solid, fanless thin mini-itx with a x86 amd64 for $10 more.
About Zeroshell, the opensource part bothered me also… but once you install it, you accept a part of it. Zeroshell is mechanizing linux and opensource software. You can check manually with a shell every firewall/load-balancing rule injected and monitor the work at a low level.
What is still bothering me is the monolithic binary-only approach, which is not reassuring. You should be able to package yourself a zeroshell image by compiling opensource software with verified location and only adding the binaries for the closed source interface and administration… perhaps Fulvio (the author) will read this.
It seems you only know the Raspberry Pi (these things are the only ones in my collection of over 40 different ‘small ARM dev boards’ that rely on crappy USB Ethernet) and the real question for me is why I should trust in a security appliance that relies on unreliable kernels and neither allows me to build the solution from source nor provides any transparency what’s happening inside.
@tkaiser
I don’t have the Rasp Pi, started in 2012 to play with a allwinner a10 (guillaumeplayground.net).
But you are right, I am not a collector of ARM dev boards. I just have a10 and some cubietrucks.
Last month I needed a network appliance, LEDE did the job on a bunch of netgear.
I don’t see anymore the hype in using a $60-$80 board, with a too small community, not really bullet proof or well designed, to try to do reliable stuff you can do with small low cost x86 amd64 for nearly the same price. I have done some kernel work on the a10 and I have seen a bit of the laziness and approximation put in the implementation and production of the great ARM architecture.
Time changes and low cost ARM dev boards are now more reliable but not enough for my taste.
The real change for me will come when sub-$100 desktop ARM boards go mainstream… I hope one day…
About zeroshell, you are absolutely right. It lacks a lot of transparency in the building process, you should be able to build your own iso from trusted source for the opensource parts of it (including the kernel).
But despite this, it works great, that’s my point about this post.
Rpi router sounds useful. Sometimes people want more processing power and even tensor/AI stuff so a board with open GPU works better. Rpi supports usb3 gigabit dongles. Maybe not at full speed, but gigabit nevertheless. Sufficient for home use.
I wish there was a supported Quagga (ex. GNU Zebra) routing package in the Raspbian repository (last time I looked there wasn’t). Quagga supports OSPF/BGP/RIP & lots more.
https://en.wikipedia.org/wiki/Quagga_(software)
But while Quagga can live in Linux it is typically deployed in xBSD based routers which take advantage of BSD’s powerful pf/altq firewall/shaper/scheduler, that’s why pfSense is BSD based. [pf/altq can be ported to Linux to live along side netfilter/iptables, but now you’re really creating a “Frankendistro”.] If you’re building a router, you probably want to start with FreeBSD for development and OpenBSD for production on x86, and NetBSD on ARM.
https://en.wikipedia.org/wiki/PF_(firewall)
https://en.wikipedia.org/wiki/ALTQ
AFAIK all three BSD’s run Quagga. NetBSD already runs on the Raspberry Pi:
http://www.raspbsd.org/
https://www.raspberrypi.org/forums/viewtopic.php?f=86&t=197082&sid=92363d66d48ec02a1de3cd017644fc67
So there you have it, Raspberry Pi running NetBSD with Quagga and pf/altq. That’s what the Big Iron router boxes run (they just slap their own branding on the box and suck your wallet dry).
As a final act, scrape the GUI off of ZeroShell and slap it on that shiny new RPi/NetBSD router 😉
If only pfSense would support ARM via NetBSD. It’s not just Raspberry Pi any more, we are seeing more ARM boards these days with multiple network interfaces that would make inexpensive yet powerful routers. Believe me, they’ve been asked many times. But the pfSense people don’t seem interested (yet). See this:
https://forum.pfsense.org/index.php?topic=59718.15
@cnxsoft: you should really overthink putting any information in the first sentence/paragraph of your blog posts. At least majority of commenters usually skip this completely.
@tkaiser
I’ve already changed that. Instead of 2 or 3 lines, I now try to write paragraphs before adding an illustration.
Other websites have the same kind of format.
Before I’ve had cases of people misunderstood what written in the middle of the post. Anyway, I have no plan to further change the way I do it, unless I get hard evidence there’s a better way.