Google Research has been working on its own Rust-based operating system called KataOS and designed to secure embedded systems that run Machine Learning (ML) applications.
There has been a lot of talk about the Rust programming language in recent times, since it offers about the same level of performance as C programming but helps programmers write more secure code with built-in prevention against buffer overflows for instance. It has gained a lot of traction over the years, and Linux 6.1 will be the first kernel release to include Rust code.
Google Research noticed that system security is often treated as a feature that can be added to existing systems either by software or an extra security chip. But in a world, where more and more of our private data is exposed to the world through the Internet, it is not good enough, so the company developed KataOS open-source, secure operating system optimized for embedded devices that run ML applications, and decided to use Rust for most of the code.
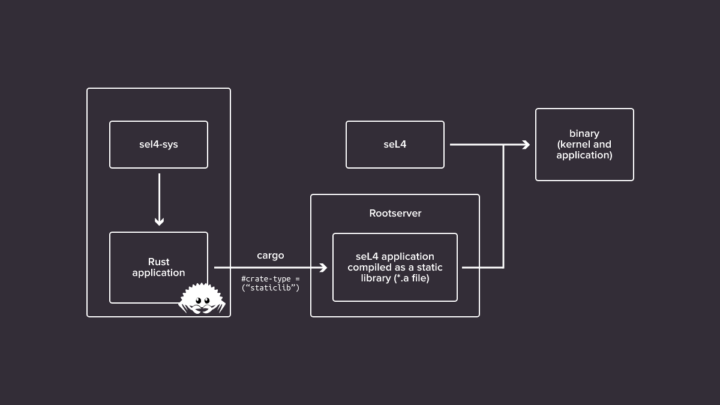
KataOS is based on seL4 microkernel because it is mathematically proven secure with guaranteed confidentiality, integrity, and availability. Antmicro also helped by enabling Rust applications for the seL4 microkernel using the Renode simulator. Google provides more details about the security aspect of the operating system:
Through the seL4 CAmkES framework, we’re also able to provide statically-defined and analyzable system components. KataOS provides a verifiably-secure platform that protects the user’s privacy because it is logically impossible for applications to breach the kernel’s hardware security protections and the system components are verifiably secure. KataOS is also implemented almost entirely in Rust, which provides a strong starting point for software security, since it eliminates entire classes of bugs, such as off-by-one errors and buffer overflows.
Sparrow is a reference implementation for KataOS designed for Ambient ML applications. Project Sparrow is hosted on GitHub and consists of the following repositories:
- camkes-tool – seL4’s camkes-tool repository with additions to support KataOS services
- capdl – seL4’s capdl repository with addition for KataOS services and the KataOS rootserver (a replacement for capdl-loader-app that is written in Rust and supports hand-off of system resources to the KataOS MemoryManager service)
- kernel – seL4’s kernel with drivers for Sparrow’s RISC-V platform and support for reclaiming the memory used by the KataOS rootserver
- kata frameworks for developing in Rust, and (eventually) the KataOS system services
- scripts – support scripts including build-sparrow.sh
The company further explains that Sparrow includes a logically-secure root of trust built with OpenTitan on a RISC-V architecture, but they’re using 64-bit Arm platform in QEMU for the initial release. KataOS and Sparrow are work-in-progress, and the goal is to fully open-source hardware and software designs for the project.
Additional information may also be found in Google’s announcement.
Thanks to Christian for the tip.

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





> secure by design
> designed by Google
Please pick one.