Updating the BIOS/UEFI binary usually requires a reboot, but Intel is working on changing that, at least on Linux servers for now, with the Intel Seamless Update aiming to carry out system firmware updates (e.g. UEFI) at run-time without having to reboot, a bit like what Canonical does with the Ubuntu Livepatch service, but at a lower level in the software stack.
Intel submitted a patch that “Introduces Platform Firmware Runtime Update and Telemetry drivers” to the Linux kernel mailing list a couple of days ago with the description reading in part:
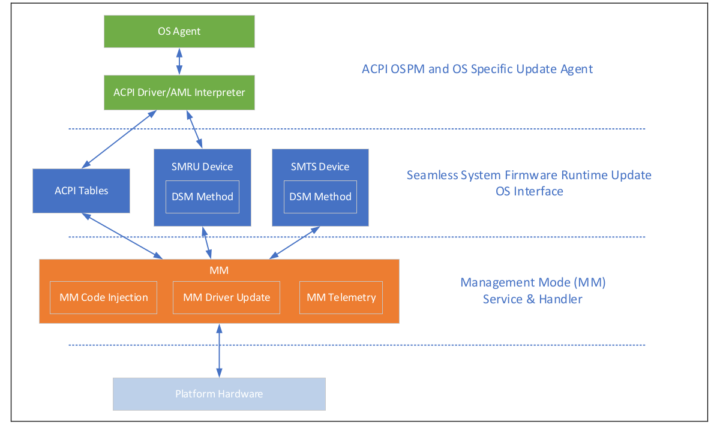
High Service Level Agreements (SLAs) requires that the system runs without service interruptions. Generally, system firmware provides runtime services such as RAS (Reliability, Availability and Serviceability) features, UEFI runtime services and ACPI services. Currently if there is any firmware code changes in these code area, the system firmware update and reboot is required. Example of bug fix could be wrong register size or location of the register. This means customer services are not available during the firmware upgrade, which could approach several minutes, resulting in not able to meet SLAs.
Intel provides a mechanism named Management Mode Runtime Update to help the users update the firmware without having to reboot.
More details can be found in an accompanying document entitled “Intel Management Mode Firmware Runtime Update – OS Interface” that explains how Intel Seamless Update work.
The new code submitted to the Linux kernel provides the following functionalities:
- Perform a runtime firmware driver update and activate.
- Ability to inject firmware code at runtime, for dynamic instrumentation.
- Facility to retrieve logs from runtime firmware update and activate telemetry.
As mentioned in the commit message, Intel Seamless Update mainly targets Linux servers that require close to 100% uptime due to legal requirements, so it may not necessarily be enabled by default in Linux Desktop distributions anytime soon, but at least if you have an Intel-based gateway or another system that needs to run with minimal interruption there should soon be an option to avoid downtime even during critical firmware (BIOS/UEFI) updates.
Via Liliputing and Phoronix

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress





And of course, this is another way that is unable to update IME Minix, so it is quite pointless.
Cool feature. I’m wondering: Does this make BIOS upgrade less or more risky?
Runtime code injection is always risky.. of something happens to the raid, you’d be sh*t or of luck no matter if it’s hot och cold update 🙂
I’m pretty sure this reboot downtime could mitigated with another machine… Like, you’re probably using kubernetes anyway, so the load would just be higher on the other machine while it’s rebooting.
Thankfully this will be as secure as the rest of the INTEL security and remote stack.
*&^%$#@?!
Attackers are rejoicing all over the world.